Update: in recent builds of Windows the BackupToAAD-BitLockerKeyProtector PowerShell command does most of what this used to do 🙂
I recently ran into an article by Pieter Wigleven, based on an original idea of Jan Van Meirvenne that I simply have to share, and expand upon.
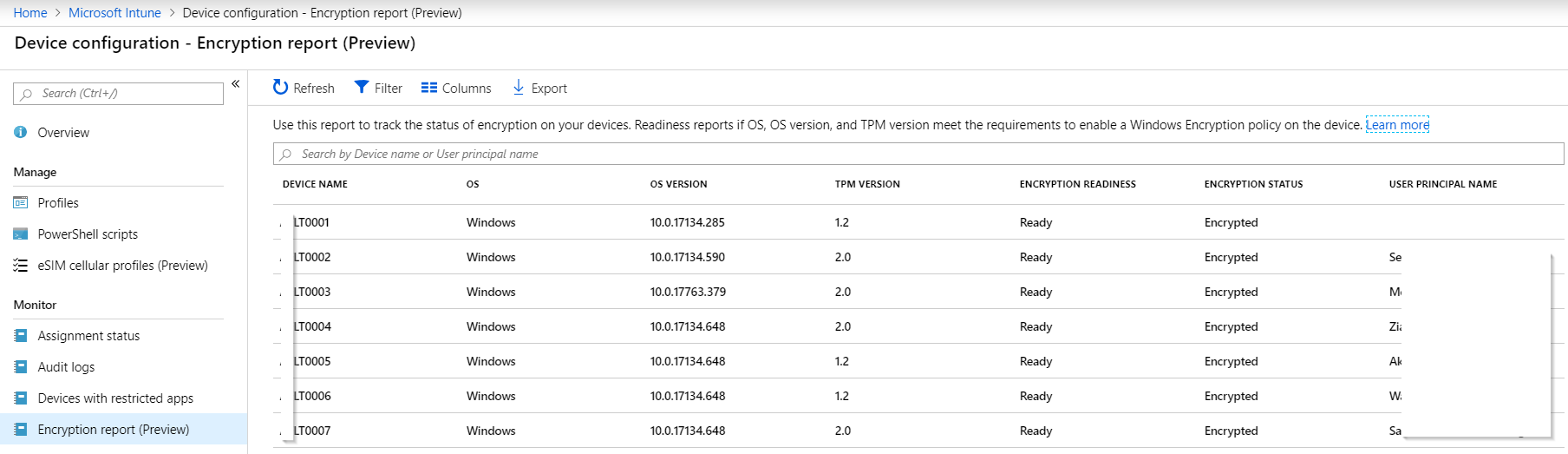
When you go cloud first, and do light MDM management of your Azure AD Joined Windows 10 devices, you will likely enable a Bitlocker policy in Intune. What you’ll quickly discover, is that your policy will not automatically enforce/enable Bitlocker on non-InstantGo capable devices.
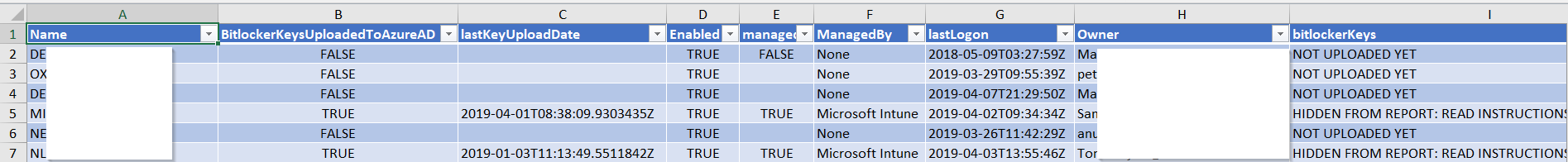
So, I expanded upon Jan and Pieter’s script to automatically enable Bitlocker on Windows 10; it has additional error handling, local logging and it will eject removable drives prior to immediately (vs reboot) encrypting your system drive. After this is started, it will register your recovery key in AzureAD. Of course all credit for the original idea goes to Jan van Meirvenne.
Powershell source file
enableBitlockerAndRegisterInAAD_v0.04.ps1 (right click, save as)
MSI file
enableBitlockerAndRegisterInAAd_v0.04.msi (right click, save as)
As Intune won’t let you deploy a Powershell script, I’ve also wrapped the script in an MSI file with Advanced Installer for you. What this will do;
- Deploy the PS1 file to the machine
- Register a scheduled task to run this PS1 file at logon each time
- Kick off the scheduled task once so a first reboot isn’t required
Advanced installer package (.aip)
enableBitlockerAndRegisterInAAD.zip (right click, save as)
Requirements
- Windows 10, AzureAD Joined
- TPM chip
- User should be local admin