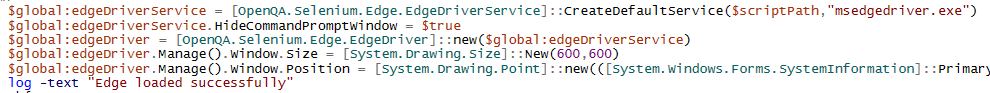
You can now download and test OnedriveMapper 5, fully based on Edge and without any dependencies on Internet Explorer (to be deprecated August 17).
Installation instructions for V5 have already been updated on the OnedriveMapper page.

You can now download and test OnedriveMapper 5, fully based on Edge and without any dependencies on Internet Explorer (to be deprecated August 17).
Installation instructions for V5 have already been updated on the OnedriveMapper page.
This August, the 17th to be precise, Microsoft 365 will stop supporting IE 11.
As OnedriveMapper 4.X uses Internet Explorer under the hood, there is a chance that functionality will break.
As Microsoft does not intend to actively block IE 11, there may be some lag until users actually begin experiencing issues with OnedriveMapper 4, and V3 may also continue to work properly as it does not use IE (in native mode).
But to ensure continuity I’ve begun testing with OnedriveMapper 5 using the Edge Webdriver and the WebView2 component.
I’m aiming to release an ‘Edge’ (Chromium) version of OnedriveMapper before August so you have ample time to test and upgrade. As always, this update will be free / open source.
ODM 5 will require Edge Chromium to be present on your endpoints.
UPDATE: LeanLAPS has finally been ‘superceded’ by Microsoft’s own LAPS 🙂 https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/introducing-windows-local-administrator-password-solution-with/ba-p/1942487
The main differences between Microsoft AAD LAPS and LeanLAPS:
LeanLAPS
Managing local admin accounts using Intune has a lot of quirks, my tele-colleague Rudy Ooms has already written extensively about this. He also wrote a PowerShell solution to rotate a specific local admin’s password and had the genius idea of using Proactive Remediations (a MEM feature) to display passwords to admins, integrated / free in the Intune Console.
However, I felt I needed a more lightweight solution that;
Thus LeanLAPS was born!
To install/use:
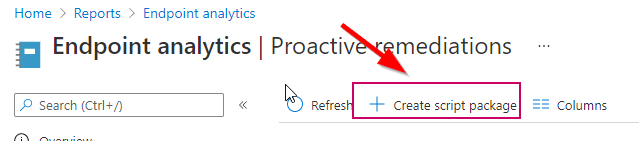
1. head into the Proactive Remediations section of MDE and click Create script package:
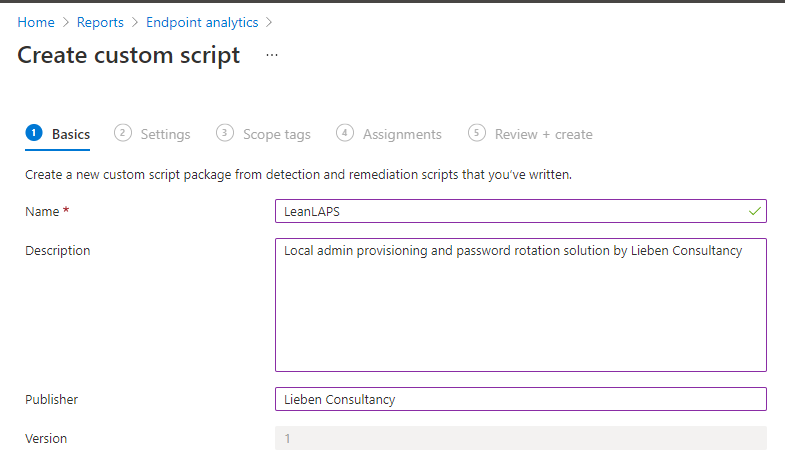
2. Fill out some details:
3. Download and doublecheck the config of LeanLAPS.ps1 (e.g. configure if other local admins should be removed, what the local admin name should be and the password length). Make sure to use NotePad++ / that the file stays UTF-8 Encoded without a BOM.
4. Set both the detection and remediation script to LeanLAPS.ps1 and run it in 64 bit:
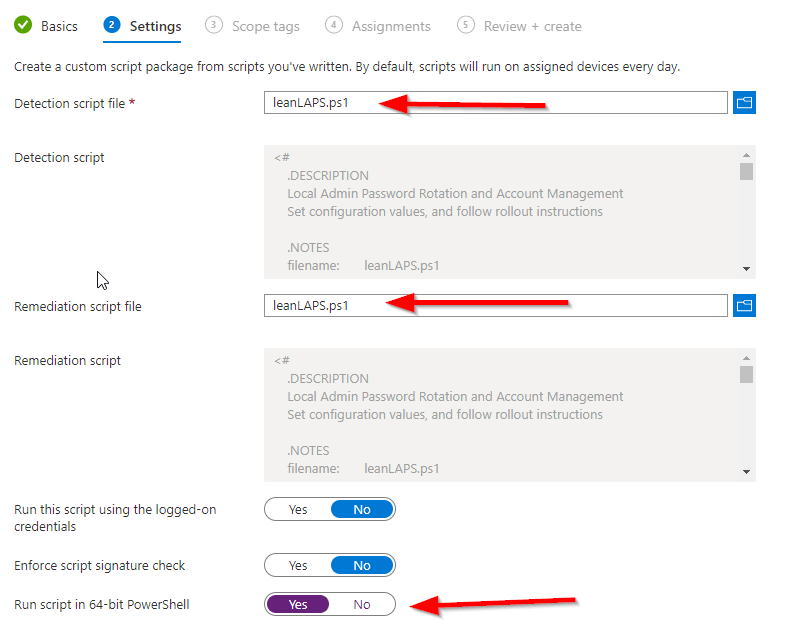
5. Assign to a group and deploy. By default it will run every day, but you can also let it run more or less frequently, which determines how often the password is reset (hourly in below example):
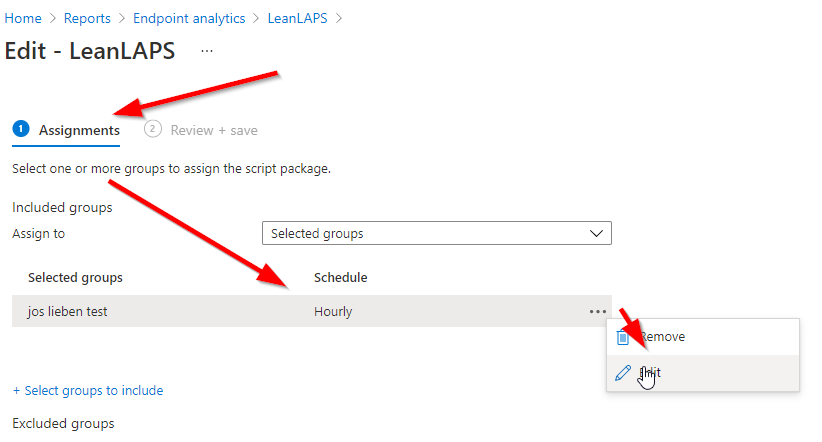
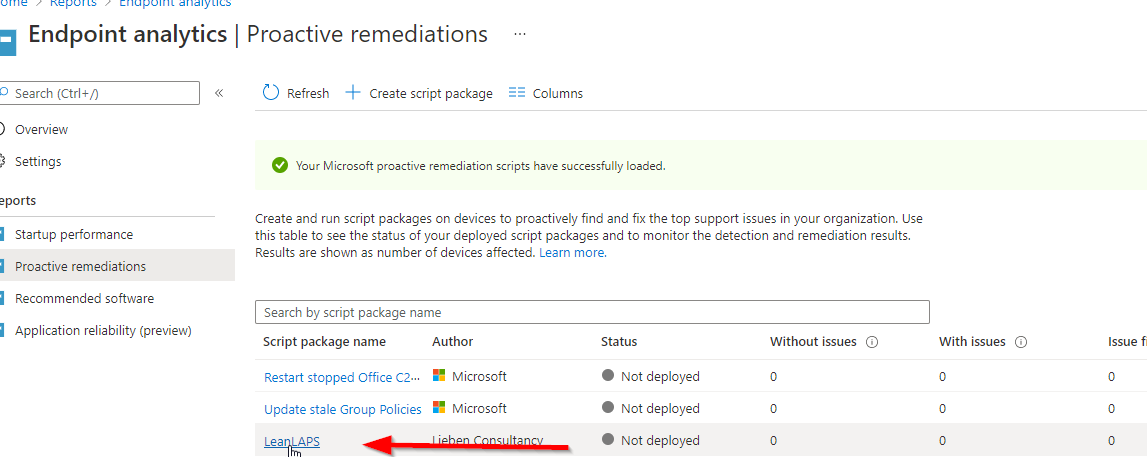
6. Deploy, and then click on the script package:
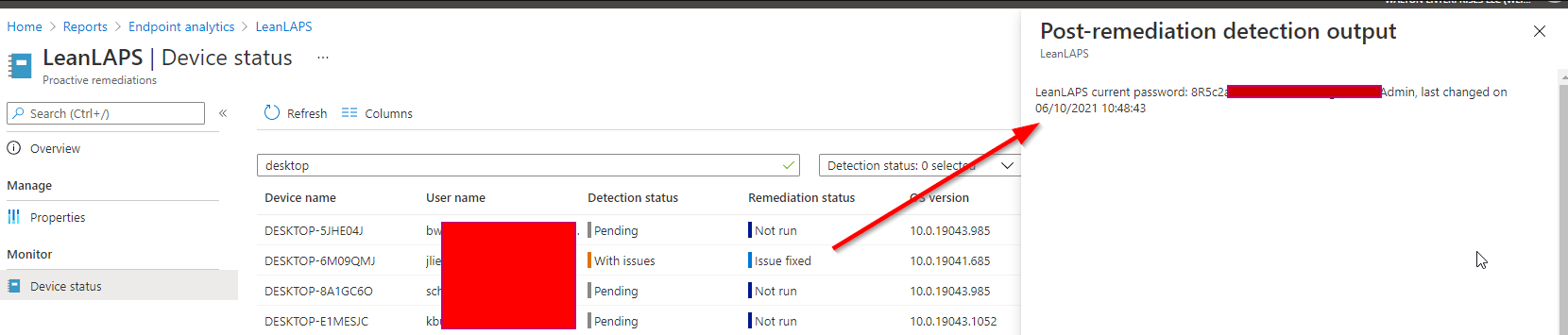
7. Go to Device status and add both output columns:
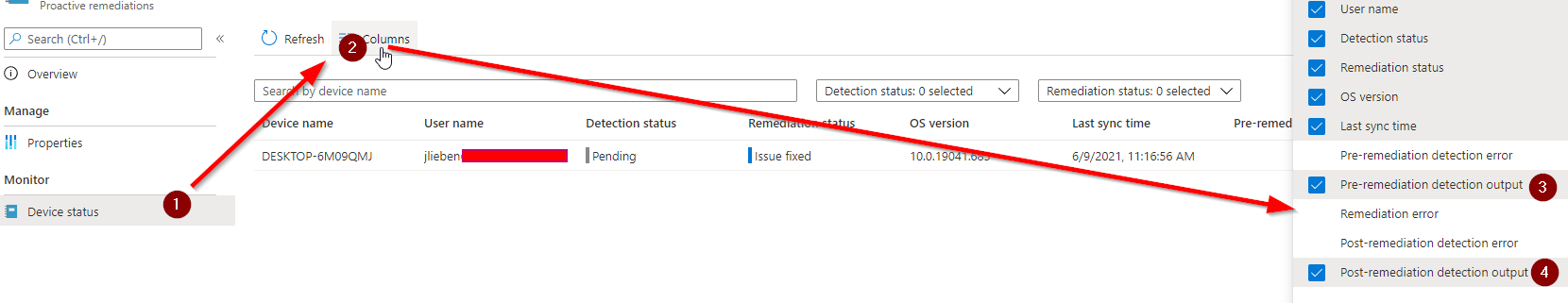
Congratulations, you can now see the current local admin passwords for all managed Windows 10 devices!
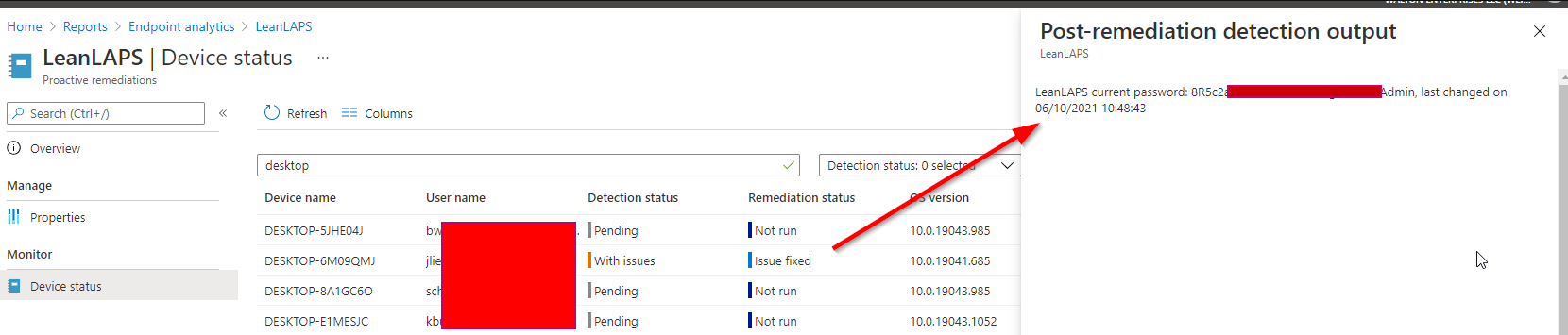
Note: if you wish to trigger a quick remediation, delete the correct keys under Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\IntuneManagementExtension\SideCarPolicies\Scripts\Execution and Reports in the client’s registry, then restart the IntuneManagementExtension service and the remediation will re-run within 5 minutes.
8. If you want to display an encrypted password in Intune, generate a public and private key and configure the resulting values in gui.ps1 and leanLAPS.ps1
9. If you don’t want LeanLAPS to remove certain preapproved admins or groups as admin, make sure to configure the $approvedAdmins variable.
RBAC
If you provide e.g. your helpdesk with the correct Intune roles, they will be able to see local admin passwords as reported by above solution:

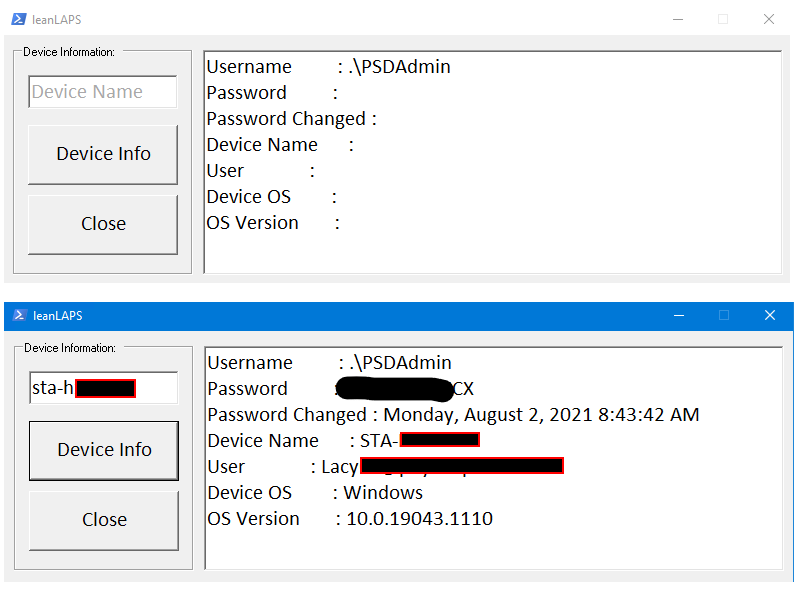
GUI
The community, in the form of Colton Lacy, also added an optional GUI frontend for LeanLAPS which you could use for e.g. helpdesk staff:
Troubleshooting
If your passwords don’t rotate correctly, check https://smsagent.blog/2021/04/27/a-case-of-the-unexplained-intune-password-policy-and-forced-local-account-password-changes/
Spent some time troubleshooting an issue deploying new VM’s to our Windows Virtual Desktop hostpool today, and since the DSC extension that adds the WVD host to the hostpool completed successfully but the VM’s didn’t join the hostpool, here’s the error for those googling it in the future:
No match for RegistrationKey found in the meta mof file
The reason the RegistrationKey never made it to the extension ended up being an expirationTime set “only” 6 hours in the future. Apparently, one of the steps isn’t actually executed in our target zone (West Europe). Setting the host pool token expiration time to 20 hours resolved above error.
The full DSC extension log in Azure:
[
{
"code": "ComponentStatus/DscConfigurationLog/succeeded",
"level": "Info",
"displayStatus": "Provisioning succeeded",
"message": "[2021-06-03 10:37:48Z] [VERBOSE] [REDACTED]: LCM: [ Start Set ] [[Script]ExecuteRdAgentInstallClient]\r\n[2021-06-03 10:37:48Z] [VERBOSE] [REDACTED]: [[Script]ExecuteRdAgentInstallClient] Performing the operation \"Set-TargetResource\" on target \"Executing the SetScript with the user supplied credential\".\r\n[2021-06-03 10:38:05Z] [VERBOSE] [REDACTED]: LCM: [ End Set ] [[Script]ExecuteRdAgentInstallClient] in 16.5940 seconds.\r\n[2021-06-03 10:38:05Z] [VERBOSE] [REDACTED]: LCM: [ End Resource ] [[Script]ExecuteRdAgentInstallClient]\r\n[2021-06-03 10:38:05Z] [VERBOSE] [REDACTED]: LCM: [ End Set ]\r\n[2021-06-03 10:38:05Z] [VERBOSE] [REDACTED]: LCM: [ End Set ] in 17.3440 seconds.\r\n[2021-06-03 10:38:05Z] [VERBOSE] Operation 'Invoke CimMethod' complete.\r\n[2021-06-03 10:38:05Z] [VERBOSE] Time taken for configuration job to complete is 17.478 seconds\r\n[2021-06-03 10:38:08Z] [VERBOSE] Performing the operation \"Start-DscConfiguration: SendMetaConfigurationApply\" on target \"MSFT_DSCLocalConfigurationManager\".\r\n[2021-06-03 10:38:08Z] [VERBOSE] Perform operation 'Invoke CimMethod' with following parameters, ''methodName' = SendMetaConfigurationApply,'className' = MSFT_DSCLocalConfigurationManager,'namespaceName' = root/Microsoft/Windows/DesiredStateConfiguration'.\r\n[2021-06-03 10:38:08Z] [VERBOSE] An LCM method call arrived from computer REDACTED with user sid S-1-5-18.\r\n[2021-06-03 10:38:08Z] [VERBOSE] [REDACTED]: LCM: [ Start Set ]\r\n[2021-06-03 10:38:08Z] [VERBOSE] [REDACTED]: LCM: [ Start Resource ] [MSFT_DSCMetaConfiguration]\r\n[2021-06-03 10:38:08Z] [VERBOSE] [REDACTED]: LCM: [ Start Set ] [MSFT_DSCMetaConfiguration]\r\n[2021-06-03 10:38:08Z] [VERBOSE] [REDACTED]: LCM: [ End Set ] [MSFT_DSCMetaConfiguration] in 0.0160 seconds.\r\n[2021-06-03 10:38:08Z] [VERBOSE] [REDACTED]: LCM: [ End Resource ] [MSFT_DSCMetaConfiguration]\r\n[2021-06-03 10:38:08Z] [VERBOSE] [REDACTED]: LCM: [ End Set ]\r\n[2021-06-03 10:38:08Z] [VERBOSE] [REDACTED]: LCM: [ End Set ] in 0.0790 seconds.\r\n[2021-06-03 10:38:08Z] [VERBOSE] Operation 'Invoke CimMethod' complete.\r\n[2021-06-03 10:38:08Z] [VERBOSE] Set-DscLocalConfigurationManager finished in 0.194 seconds."
},
{
"code": "ComponentStatus/DscExtensionLog/succeeded",
"level": "Info",
"displayStatus": "Provisioning succeeded",
"message": "[2021-06-03 10:37:23Z] Creating Working directory: C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\bin\\..\\DSCWork\\Configuration.0\r\n[2021-06-03 10:37:23Z] Downloading configuration package\r\n[2021-06-03 10:37:24Z] Downloading https://raw.githubusercontent.com/Azure/RDS-Templates/master/ARM-wvd-templates/DSC/Configuration.zip to C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\bin\\..\\DSCWork\\Configuration.0\\Configuration.zip\r\n[2021-06-03 10:37:41Z] Extracting Configuration.zip\r\n[2021-06-03 10:37:41Z] Looking for the definition of the configuration function.\r\n[2021-06-03 10:37:41Z] Executing C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\bin\\..\\DSCWork\\Configuration.0\\Configuration.ps1\r\n[2021-06-03 10:37:41Z] Preparing configuration arguments and configuration data.\r\n[2021-06-03 10:37:41Z] Creating MOF files.\r\n[2021-06-03 10:37:41Z] Executing the configuration function to generate the MOF files.\r\n[2021-06-03 10:37:42Z] Verifying metaconfiguration for reboot information...\r\n[2021-06-03 10:37:42Z] Backing up C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\DSCWork\\Configuration.0\\AddSessionHost\\localhost.meta.mof\r\n[2021-06-03 10:37:42Z] No match for RegistrationKey found in the meta mof file\r\n[2021-06-03 10:37:42Z] WMF 5 or newer, Injecting RebootNodeIfNeeded = False and ActionAfterReboot = \"StopConfiguration\"\r\n[2021-06-03 10:37:42Z] Executing Set-DscLocalConfigurationManager...\r\n[2021-06-03 10:37:44Z] Settings handler status to 'transitioning' (C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\Status\\0.status)\r\n[2021-06-03 10:37:47Z] Settings handler status to 'transitioning' (C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\Status\\0.status)\r\n[2021-06-03 10:37:47Z] Get-DscLocalConfigurationManager: \r\n\r\nActionAfterReboot : StopConfiguration\r\nAgentId : ADF6E52A-C457-11EB-9BDA-000D3A2633E7\r\nAllowModuleOverWrite : False\r\nCertificateID : \r\nConfigurationDownloadManagers : {}\r\nConfigurationID : \r\nConfigurationMode : ApplyOnly\r\nConfigurationModeFrequencyMins : 15\r\nCredential : \r\nDebugMode : {NONE}\r\nDownloadManagerCustomData : \r\nDownloadManagerName : \r\nLCMCompatibleVersions : {1.0, 2.0}\r\nLCMState : Idle\r\nLCMStateDetail : \r\nLCMVersion : 2.0\r\nStatusRetentionTimeInDays : 10\r\nSignatureValidationPolicy : NONE\r\nSignatureValidations : {}\r\nMaximumDownloadSizeMB : 500\r\nPartialConfigurations : \r\nRebootNodeIfNeeded : False\r\nRefreshFrequencyMins : 30\r\nRefreshMode : PUSH\r\nReportManagers : {}\r\nResourceModuleManagers : {}\r\nPSComputerName : \r\n\r\n\r\n\r\n\r\n[2021-06-03 10:37:47Z] Executing Start-DscConfiguration...\r\n[2021-06-03 10:37:47Z] Settings handler status to 'transitioning' (C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\Status\\0.status)\r\n[2021-06-03 10:38:07Z] Settings handler status to 'transitioning' (C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\Status\\0.status)\r\n[2021-06-03 10:38:07Z] Updating execution status (HKLM:\\SOFTWARE\\Microsoft\\Azure\\DSC\\2.83.1.0\\Status)\r\n[2021-06-03 10:38:07Z] LCM state is Idle\r\n[2021-06-03 10:38:07Z] DSC configuration completed.\r\n[2021-06-03 10:38:07Z] Resetting metaconfiguration...\r\n[2021-06-03 10:38:07Z] Restoring C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\DSCWork\\Configuration.0\\AddSessionHost\\localhost.meta.mof.bk...\r\n[2021-06-03 10:38:07Z] Executing Set-DscLocalConfigurationManager...\r\n[2021-06-03 10:38:07Z] Settings handler status to 'transitioning' (C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\Status\\0.status)\r\n[2021-06-03 10:38:10Z] Settings handler status to 'transitioning' (C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\Status\\0.status)\r\n[2021-06-03 10:38:10Z] Get-DscLocalConfigurationManager: \r\n\r\nActionAfterReboot : ContinueConfiguration\r\nAgentId : ADF6E52A-C457-11EB-9BDA-000D3A2633E7\r\nAllowModuleOverWrite : False\r\nCertificateID : \r\nConfigurationDownloadManagers : {}\r\nConfigurationID : \r\nConfigurationMode : ApplyOnly\r\nConfigurationModeFrequencyMins : 15\r\nCredential : \r\nDebugMode : {NONE}\r\nDownloadManagerCustomData : \r\nDownloadManagerName : \r\nLCMCompatibleVersions : {1.0, 2.0}\r\nLCMState : Idle\r\nLCMStateDetail : \r\nLCMVersion : 2.0\r\nStatusRetentionTimeInDays : 10\r\nSignatureValidationPolicy : NONE\r\nSignatureValidations : {}\r\nMaximumDownloadSizeMB : 500\r\nPartialConfigurations : \r\nRebootNodeIfNeeded : True\r\nRefreshFrequencyMins : 30\r\nRefreshMode : PUSH\r\nReportManagers : {}\r\nResourceModuleManagers : {}\r\nPSComputerName : \r\n\r\n\r\n\r\n\r\n[2021-06-03 10:38:10Z] Settings handler status to 'success' (C:\\Packages\\Plugins\\Microsoft.Powershell.DSC\\2.83.1.0\\Status\\0.status)"
},
{
"code": "ComponentStatus/Metadata/succeeded",
"level": "Info",
"displayStatus": "Provisioning succeeded",
"message": "VMUUId=6DFC142E-0A63-41D1-BE3E-31F5D0D9D8A3;AgentId=BDF6E52A-C427-12EB-9BDA-001D3A2633E7;"
}
]