UPDATE: LeanLAPS has finally been ‘superceded’ by Microsoft’s own LAPS 🙂 https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/introducing-windows-local-administrator-password-solution-with/ba-p/1942487
The main differences between Microsoft AAD LAPS and LeanLAPS:
- MS Won’t enable the account if it’s disabled.
- MS Won’t create the account if it doesn’t exist.
- MS Won’t add it to Administrators group if it’s not a member.
- MS Won’t remove accounts from Administrators group if they’re not supposed to be there.
- MS has an AAD integrated GUI and RBAC
- LeanLAPS requires P2 licensing because it used Proactive Remediations
LeanLAPS
Managing local admin accounts using Intune has a lot of quirks, my tele-colleague Rudy Ooms has already written extensively about this. He also wrote a PowerShell solution to rotate a specific local admin’s password and had the genius idea of using Proactive Remediations (a MEM feature) to display passwords to admins, integrated / free in the Intune Console.
However, I felt I needed a more lightweight solution that;
- does not require/modify registry keys
- does not store the password locally
- can encrypt the password if desired
- does not need separate detection and remediation scripts
- automatically provisions a local admin account
- can remove any other local admin accounts if desired
- can whitelist approved admins or groups from AzureAD or Active Directory
- is language/locale-agnostic (e.g. ‘Administrators’ vs ‘Administradores’….)
Thus LeanLAPS was born!
To install/use:
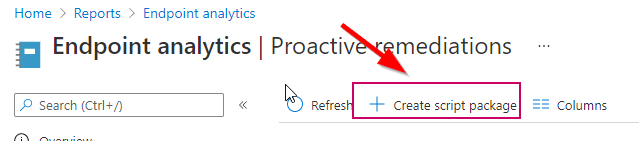
1. head into the Proactive Remediations section of MDE and click Create script package:
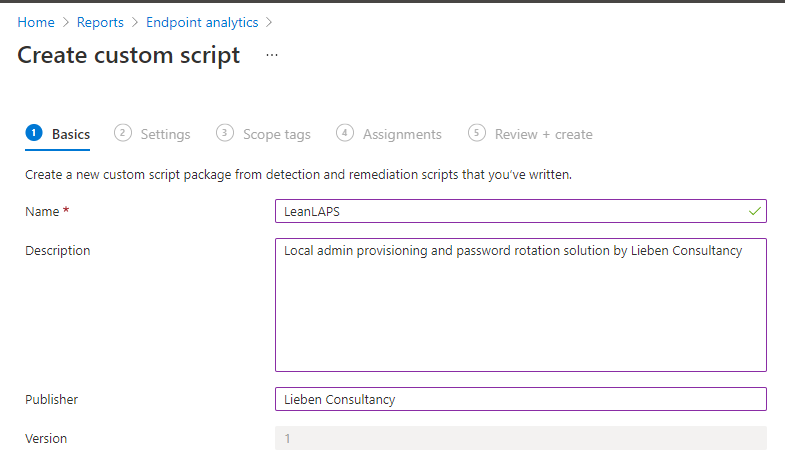
2. Fill out some details:
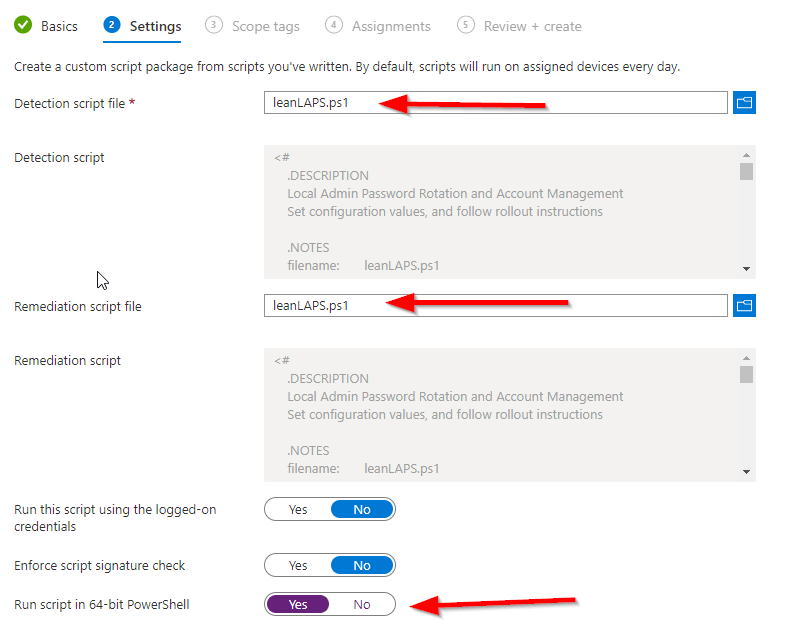
3. Download and doublecheck the config of LeanLAPS.ps1 (e.g. configure if other local admins should be removed, what the local admin name should be and the password length). Make sure to use NotePad++ / that the file stays UTF-8 Encoded without a BOM.
4. Set both the detection and remediation script to LeanLAPS.ps1 and run it in 64 bit:
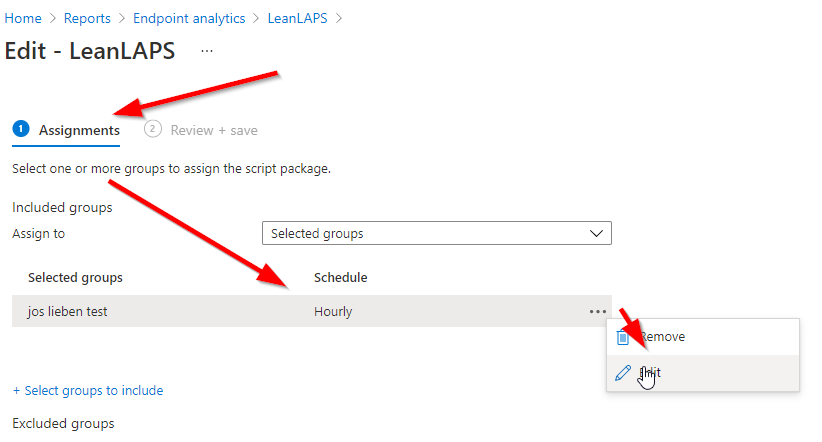
5. Assign to a group and deploy. By default it will run every day, but you can also let it run more or less frequently, which determines how often the password is reset (hourly in below example):
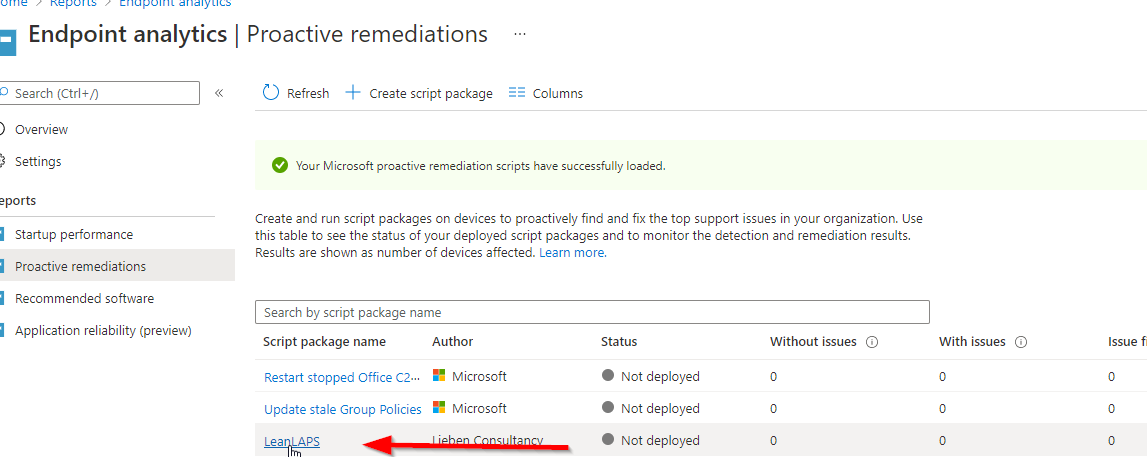
6. Deploy, and then click on the script package:
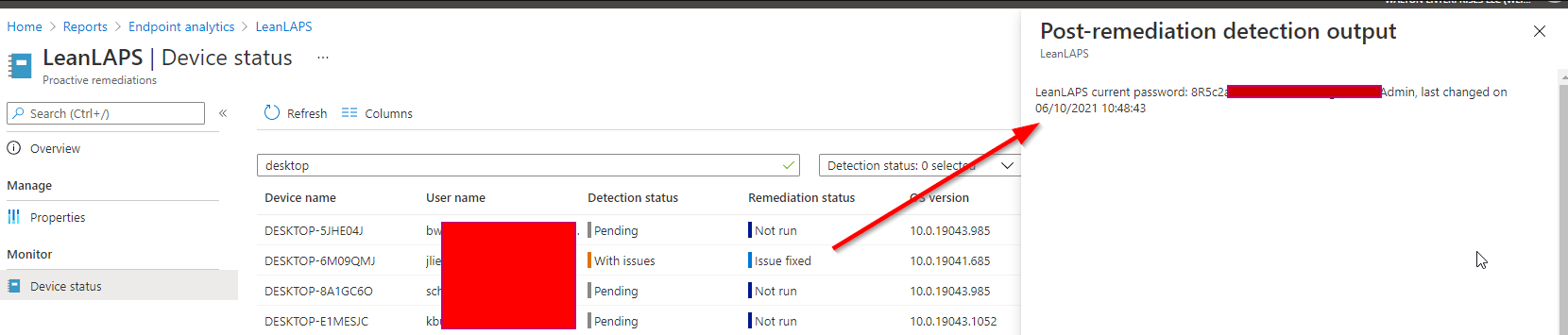
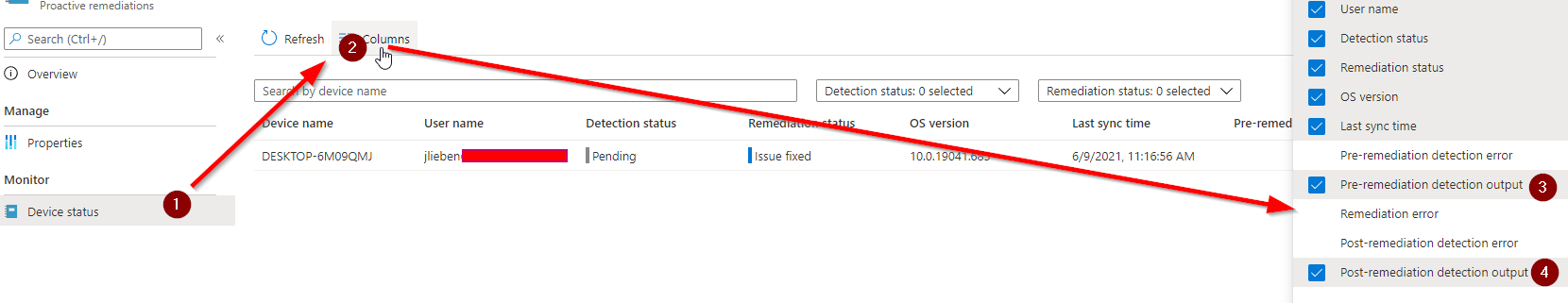
7. Go to Device status and add both output columns:
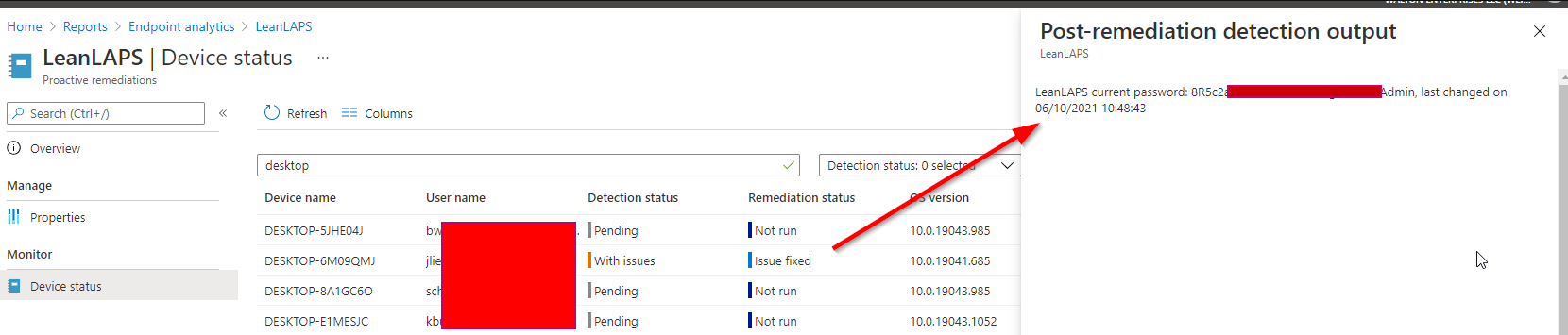
Congratulations, you can now see the current local admin passwords for all managed Windows 10 devices!
Note: if you wish to trigger a quick remediation, delete the correct keys under Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\IntuneManagementExtension\SideCarPolicies\Scripts\Execution and Reports in the client’s registry, then restart the IntuneManagementExtension service and the remediation will re-run within 5 minutes.
8. If you want to display an encrypted password in Intune, generate a public and private key and configure the resulting values in gui.ps1 and leanLAPS.ps1
9. If you don’t want LeanLAPS to remove certain preapproved admins or groups as admin, make sure to configure the $approvedAdmins variable.
RBAC
If you provide e.g. your helpdesk with the correct Intune roles, they will be able to see local admin passwords as reported by above solution:

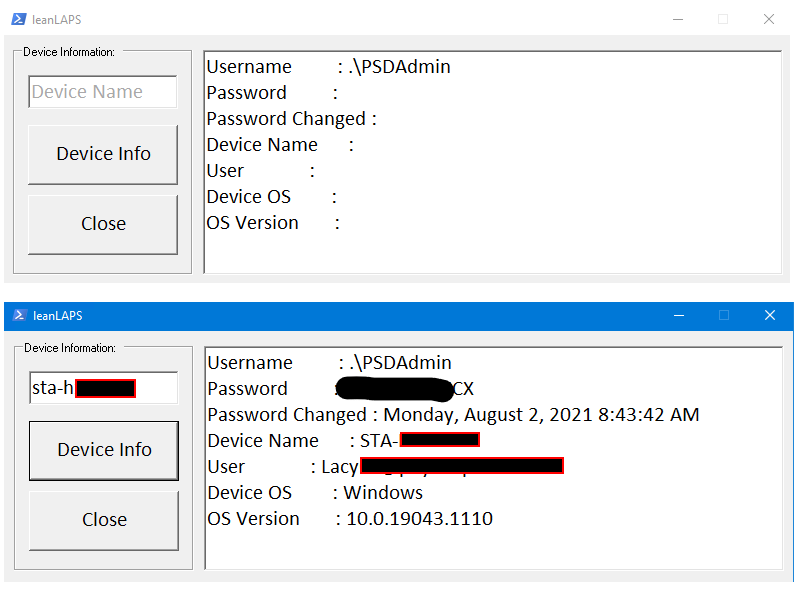
GUI
The community, in the form of Colton Lacy, also added an optional GUI frontend for LeanLAPS which you could use for e.g. helpdesk staff:
Troubleshooting
If your passwords don’t rotate correctly, check https://smsagent.blog/2021/04/27/a-case-of-the-unexplained-intune-password-policy-and-forced-local-account-password-changes/
Awesome work! Is there any way we can keep the 2 azure AD SIDs for global and local admins that get added when a machine is joined to azure while removing any other local admin? We want to keep the ability to use the local admin group via azure portal while removing any previous local admins. When running the script I notice my azure ad machines lose their global\local admin SIDS.
Updated to the latest script and getting this output now……
{“Username”:”user”,”SecurePassword”:”4f*=f8zDxR”,”Date”:{“value”:”\/Date(1665494623434)\/”,”DisplayHint”:2,”DateTime”:”Tuesday, October 11, 2022 9:23:43 AM”}}
it used to be like this before……
LeanLAPS current password: a0!i4Yay(G for user, last changed on 04/07/2022 17:01:01
Anyway to change it back to old view?
Microsoft makes this such a pain in the neck. Then to add insult to injury your solution requires additional licensing above what we already have, just to implement a feature that should already exist.
SIGH.
Nice work! I’ve upgraded your solution with encryption the password with public key, and sending it securely . it can then be decrypted with private key , so the password is never exposed in user’s computer, on the post to intune or in the intune itself. (and so there is no need to delete intune logs to cover up tracks 🙂
also found that some computers having error changing password with error 3221226252 .
i was able to resolve it by splitting the line where ConvertTo-SecureString happens, so i first create the secure-string and then change the administrator password .
Looks great, thank you.
We are soon to decommission AD and go Azure cloud only.
Can I confirm if this solution still requires AD in the way LAPS does?
i.e. I’m looking for a solution of local admin password management that will work without AD
Thanks, Jos. This is awesome! I’m getting the following error – have updated the variable $localAdminName = “CustomAccount” New-LocalUser : A positional parameter cannot be found that accepts argument ‘True’. At C:\WINDOWS\IMECache\HealthScripts\601ec906-1ca6-4958-8678-089ca2e3217e_1\detect.ps1:53 char:19 + … ocalAdmin = New-LocalUser -PasswordNeverExpires $True -AccountNeverEx … + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidArgument: (:) [New-LocalUser], ParameterBindingException + FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.PowerShell.Commands.NewLocalUserCommand C:\WINDOWS\IMECache\HealthScripts\601ec906-1ca6-4958-8678-089ca2e3217e_1\detect.ps1 : Something went wrong while processing the local administrators group Cannot validate argument on parameter ‘Member’. The argument is null or empty. Provide an argument that is not null or empty, and then try the command again. + CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException… Read more »
can someone help with this ?
That is very clever. I like it and see a lot of usage and need for this. Great job.
Hi, nice work for this script. I’m just confirming that this output is correct as it is not the same as the output shown above? I assume this is for the GUI and serves the same result nonetheless for the remediation output.
{“Username”:”OurLocalAdmin”,”SecurePassword”:”xxxxxxxxxxxxxxxx”,”Date”:{“value”:”\/Date(1665462513995)\/”,”DisplayHint”:2,”DateTime”:”Tuesday, 11 October 2022 2:28:33 PM”}}
Thanks for the script. I have adapted the script so that our helpdesk does not have to search for the device name via the web, but can use it directly in the GUI.
$user = Get-AzureADUser -SearchString $inputBoxUsr.Text
$devicenames= Get-AzureADUserRegisteredDevice -ObjectId $user.ObjectId -All $true | ft DisplayName
Then put the whole thing into the output box and link it to an additional button. Then you can search for a user and all linked devices will be searched in Azure AD. The device name can be copied out of there.
Let’s be clear… LeanLAPS is NOT superseded by Microsoft’s implementation at all. In fact, it’s grossly inferior. Microsoft’s implementation: Won’t enable the account if it’s disabled. Won’t create the account if it doesn’t exist. Won’t add it to Administrators group if it’s not a member. Won’t remove accounts from Administrators group if they’re not supposed to be there. That’s pretty freaking lame, if we’re being honest. The only good thing it CAN do is provide a readable password directly from Azure and Intune portals without a GUI tool. Which makes me wonder… could LeanLAPS be updated to store its password… Read more »
Awesome solution, really appreciate all the hard work putting this together. I am running into an issue that I haven’t been able to resolve yet however. When I run the GUI and type in a device name, it shows the password for a completely different device. Any help in resolving this would be greatly appreciated!
Thank you so much for putting this together! I am getting a strange error when using the GUI though. When I attempt to obtain the password for a particular device from the GUI, I receive the error Exception calling “PerformClick” with “0” argument(s): “Invalid JSON primitive:Invalid JSON primitive: LeanLAPS. Note that I named the proactive remediation script in Intune LeanLAPS. If anyone has any insight to this error it your assistance would be greatly appreciated!
First of all, thank you very much! We were looking for this solution 🙂 We modified it to encrypt the password, so there is no need to create the scheduled task during the Proactive Remediation. First, you generate and keep the private and public keys: ## Generate key pair $RSA = New-Object System.Security.Cryptography.RSACryptoServiceProvider(2048) $private = $rsa.ExportCspBlob(1) $private -join "," $public = $rsa.ExportCspBlob(0) $public -join "," Then, in the script you can add a function like below with your public key as a string separated by commas. ## Encrypt Password using the Public key Function Encrypt-Password ($password)… Read more »
Just a litle heads up
$onlyRunOnWindows10 = $True #buildin protection in case an admin accidentally assigns this script to e.g. a domain controller
[Environment]::OSVersion.Version.Major -ne 10
Windows Server 2016 and 2019 will report 10, so it will not prevent a server to run it.
Great solution BTW, thank you
Great solution, very nice! I have two questions:
First, you wrote under 5. “Assign to a device group (user groups won’t work)” -> I tried it with a user group in my tests and it works with no issues. Could it be that your advice pointed to a earlier version of the tool?
Second, the copyright says “not for commercial use without written consent” -> what is the correct way the get this consent from you? We’d very much like to use your tool in our production environment.
Hi Jose,
How can I Make sure that the password always contain the password policy requirements. See below error on one of the machines:
Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.
As always, thanks for the amazing contribution! I was just about to set up the LAPS azure blob storage method I’ve read about elsewhere until I noticed your link on the user voice.
Just noticed one thing, we hot-desk and in my HAADJ environment if there is more than one user logged in to a workstation (switch user is enabled). The detection and remediation runs twice in succession, once against each active user. Not a big issue but just thought I’d flag it for your attention.
Hi Jos,
Great, thanks for this!
I’ve tried to use the script, but it fails at my machines on creating the user when it does not exist.
The error is: Cannot validate argument on parameter ‘Member’. The argument is null or empty. Provide an argument that is not null or empty and try again.
When running the scripts manually and asking the value of $localadmin it’s empty.
I was using Lean laps until recently when i’ve move to Microsoft version. However I’m having a problem that LeanLaps seems to be still removing other local admins (except the built in one)
I found a scheduled task on the computers, which I’ve removed (the remediations scripts are gone from intune already). Is there anything else that needs to be removed to “uninstall” leanlaps?
Does users need E3/E5 licenses like microsoft says for proactive remediations.We have 200 devices and now it stopped working for most of them.
[…] LeanLAPS […]
How is the password sent between the local machine and Intune, and what is the command that does this ?
Running into an issue with the script not running on all devices of an assigned group. Out of 20 devices in the group, only 14 show up under Device Status of the proactive remediation script overview. I confirmed that this is simply not an Intune display/GUI issue. I checked a device that is a member of the assigned group but now showing up in the Device Status list and confirmed that it is not having its password updated. Why would Intune ignore 6 devices in the assigned group/not run the script on them?
When i run the:
Set-LocalUser -Name ‘Administrator’ -Password $newPwdSecStr -AccountNeverExpires -PasswordNeverExpires $True -UserMayChangePassword $True
I get an Error:
Microsoft.PowerShell.Commands.InternalException: An unspecified error occurred: status = 3221266571
It makes no difference if i run as admin or system, and the wierd part is that i only get this error on 5% of the computers..
Have anyone seen this before and know someting about it?
I’ve been using this solution for a couple of weeks now. But I started seeing some endpoint giving me this Post-remediation detection output:
REDACTED.
Can anyone suggest what i need to do to resolve this?
Hi, I just run the script , it failed and I’m getting the error below. Any help will be appreciated. Pre-remediation detection error LeanLAPS pty\n blobs(paths: [$filePath], ref: $ref) {\n __typename\n nodes {\n __typename\n id\n webPath\n name\n size\n rawSize\n rawTextBlob @include(if: $shouldFetchRawText)\n fileType\n language\n path\n blamePath\n editBlobPath\n gitpodBlobUrl\n ideEditPath\n forkAndEditPath\n ideForkAndEditPath\n codeNavigationPath\n projectBlobPathRoot\n forkAndViewPath\n environmentFormattedExternalUrl\n environmentExternalUrlForRouteMap\n canModifyBlob\n canCurrentUserPushToBranch\n archived\n storedExternally\n externalStorage\n externalStorageUrl\n rawPath\n replacePath\n pipelineEditorPath\n simpleViewer {\n fileType\n tooLarge\n type\n renderError\n }\n richViewer {\n fileType\n tooLarge\n type\n renderError\n }\n }\n }\n }\n }\n}\n”‘ in expression or statement. At C:\Windows\IMECache\HealthScripts\6c8670a6-dee3-48b5-95b7-c9544f7a623b_1\detect.ps1:24 char:1421 + … nderError\n }\n }\n }\n }\n }\n}\n”,”variabl … +… Read more »
In the case where a user completely loses internet connection, does the local admin password get stored locally on the device, or will it need to ping AzureAD for the password? Trying to play around with how often the remediation should happen, my thinking is if we have a user with no internet connection, in a break glass scenario, we can provide them with credentials to allow them to troubleshoot. Say the password is set to change every 7 days and on the 5th day the user loses internet connection, we can still provide credentials. Am I wrong in my thinking?
I’ve been using this solution for a couple of weeks now. But I started seeing some endpoint gving me this Post-remediation detection output:
REDACTED.
@ Jos Lieben can you please advise why this would be?
the device has set a new local admin password within the registry but intune is not syncing it in the report. still displays old password. last sync was 5 minutes ago. any remedy for this?
Hello, We are trying to use this in a 6000 + device environment. I can see the device is having the password changed. The password is being encrypted and store in the proactive remediation output. How ever when i run the gui and search for the device it can’t find any device. I can see it recursing through all the devices but resulting in no match. Any Thoughts?
Hi! I’m experimenting with this. So far so good (I’m still quite noob with Windows so I don’t quite understand the allowed admin SID part).
One thing I noticed is that the device did not remove another local admin account even though I set it to $true. It did however, create the new account without issue.
Is there anything else that I need to do? Perhaps it has to do with the SID part? Thanks!
Hey Jos,
Trying to get the $approvedAdmins to work. I ran the command to get the SID of the global admin I want to add as the administrator. I added the SID to the script but when I try to elevate to admin it is saying “the requested operation requires elevation.” I also tried creating a device group in azure and adding the correct accounts to it, but that doesn’t work either. Any ideas?
Jos, great script. I wan’t to implement this company wide but I have one issue with the pro-active remediation schedule in Intune. The sheduling options in Intune are limited to Once, Every Hour and Daily. There is no way to set this to weekly or Monthly. Would be a great addition to the script that you can define how often the password is changed. For instance every 30 days or something like that.
Hi Jos. This is going to be so helpful, thank you! Quick question. The script seems to be working for me and generating a password. However, when trying to authenticate with .\LocalAdminAcccount and the generated password, I am getting an message saying “The user’s password must be changed before logging on the first time”. Am I missing a setting in the script? This is an AAD AutoPilot machine. Appreciate your help!
Hi Jos. Great script. Is there a way to get the time entries to be local time zone rather than UTC. The registry entry and the gui both show UTC values.
Hello, what is it when the GUI does not find a device?
Message: “Device name not found or remediation did not yet run”
Am I missing permissions?
Post-remediation detection output are available.
HI, GETTING THIS ERROR
PLEASE HELP
Excellent script and makes my job a lot easier. However, initially I was running the script for user group everyday once and it was working fine. But later I changed it to daily and 7 days. Now most of the passwords in the Output are not working. Is there any way to investigate and troubleshoot as most of the computers are effected and it is causing severe issue.
Hi, Nice utility, however I am cautious about the output of the plain text password into the C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\AgentExecutor.log, which has NTFS ACLs as Everyone\RW and Users\RO?
Hi Jos, Great work on this, everything is superb!
Just that the script doesn’t run for some devices in my pilot group. No idea what’s causing the issue.
Also, can this work for any Managed Windows? Or just AAD Joined or HAADJ machines?
Thanks
Hi Jos,
Having an issue with the script removing AzureAD admins from the device. I only specified one global admin SID in the $approvedAdmins variable, but checking event viewer on my pilot group I see the following: Not removing S-1-5-21-xxxxx because of whitelisting. I have not included the above SID in $approvedAdmins, see the attached screenshots. Any idea what could be going on?
Hi Jos Sorry to ask again but I have a problem with leanLaps. I changed the minimum password length: $minimumPasswordLength = 15 Now I have the following problem: When the Admin get created he gets a 15-characters-password which worked fine. On the second run a 20-characters-passwort gets displayed in MDE. All local logs are correct as they say “Setting password for Admin1361 …” – “Password for Admin1361 set to a new value, see MDE”. But this new password is not working, and on this point also the old password no longer works. On the third run the same problem: a… Read more »
Hi Jos,
If the character ‘&’ is generated in a password, it’s displaying it as /u0026 in the post-remediation output. This is probably happening during the ConvertTo-Json part
Very helpful script, thank you for sharing. I tested this on our tenant and it is running nice. I have just one question about it: I can deactivate two type of local users: $removeOtherLocalAdmins $disableBuiltinAdminAccount Am I right that the disableBuiltinAdminAccount will deactivate the user “Administrator” which is built in after the Windows Installation? Am I right that the removeOtherLocalAdmins will remove the admins from the “Administrators”-Group? After running the script my own User (Intune owner of the device) was not in the “Administrators”-Group anymore. Which of this two settings removes the owner of the device? Can I prevent this… Read more »
Hello, this new update doesn’t allow consult the password with the new script. Any suggestion to solve the problem?
Hello, first of all thank you for the fantastic work.
I have a doubt where I can find the TaskName “leanLAPS_WL”?
I tried the policy and after I delete from Intune portal, next deleted the scripts from: c:\windows\IMEcache\Healthscripts but the script is still running, I search in task scheduler, but I don’t find anything?
Hello and thanks for this awesome Script.
We have the problem that the remedation is applied, whenever a (unique) user logs in to the device. The config is applied to a device group, so that is quite strange or is this intended?
We noew have to quickly look which user has logged in the last time, so we get the current password.
I would appreciate your help!
Hi Jos,
it works really great!! awesome job.
I have a question : The hour of “password change” is not correct, i have 2 hours less…
how I can correct this ? I’m not too comfortable with powershell.
Great work! In the first run it worked absolute fine, now we adjusted the password length and tried to re-run the script, but the Pre-remediation detection output throws the following error message now: Something went wrong while processing the local administrators group The Object reference was not set to an object instance.
Can anyone help me out here? I followed the instructions above until step 7.
This script has been working great for us. Recently devices are reporting in the “Post-remediation detection output” REDACTED instead of the password. Any idea what causes this?
Love it!! However, one question. We’re currently testing this out on a small collection, and we everything works as expected. However, the P/R report shows the devices have issues. Our other P/R scripts run, and then report back in no issue after remediation. Is this expected as the detection part? Image attached.
Trying to use the GUI to decrypt the password but I get the error below. I copied and pasted the public and private keys from my clipboard when they are generated from the generatkeys.ps1. I’ve also tried to copy/paste them into a txt editor and made sure they were in UTF-8 format. Anyone else run into this issue? See the end of this message for details on invoking just-in-time (JIT) debugging instead of this dialog box. ************** Exception Text ************** System.Management.Automation.MethodInvocationException: Exception calling “Decrypt” with “2” argument(s): “The parameter is incorrect. ” —> System.Security.Cryptography.CryptographicException: The parameter is incorrect. at System.Security.Cryptography.CryptographicException.ThrowCryptographicException(Int32… Read more »
HI, We have deployed LeanLaps to all the devices in our organisation and it was working well with out any issues but suddenly LeanLaps stopped working to all user devices and giving same admin password for all user devices! Please advise on this
I have the following issue with all the devices, can someone help ?
Running into an issue with the GUI – I am currently a GA (via PIM) and getting a crypto error. Any thoughts?
Great script. It works great till encounter an issue with password. We set the password update at every 180 days from Intune. The users are getting error with below prompt way before 180 days. Errro: “account restriction are preventing this user from signing in for example: blank password arent allowed, sign-in times are limited, or a policy restrtiction has been enforced” Admin has to remote in user machine and reset the password for local admin user in order to make it work. Also is it possible to force cahnge password from Intune on this local admin user? Thank you for… Read more »
[…] Doc about Proactive RemediationsProactive Remediations Solutions:LeanLaps by Jos LiebenUnpinning the Microsoft Store by Andrew TaylorUpdate Lenovo BIOS by Damian van RobaeysOther posts by […]
we are now running issue on our LEANLAPS, input device name is resulting a different device name
Just want to ask we are now seeing different result when we try to get a password of a computer.
encrypt the password or not ?
The communication between the client and intune should be already enrypted (ssl) right ?
So the only benefit with enryption is the password isnt plain text in intune correct?
Quick question, As many here sometimes I have computer with 2 entries. I first log with user A and a new entry is created. After sometime a new user login on the same computer and a 2nd entry is created. Problem is the second entry password requires a password change. Also the first entry “User A” is always re-created. So I have 2 entries User A and User B. But only password from User B works (fine for me), but why is User A still created as he doesn’t log anymore in the device? This always happen if we have… Read more »
I receive the following when running gui.ps1: (thoughts anyone) See the end of this message for details on invoking just-in-time (JIT) debugging instead of this dialog box. ************** Exception Text ************** System.Management.Automation.CmdletInvocationException: HttpRequestError —> Microsoft.Intune.PowerShellGraphSDK.PSGraphSDKException: HttpRequestError —> System.Net.Http.HttpRequestException: 400 Bad Request {“error”:{“code”:”UnknownError”,”message”:”String policy id is invalid. Provided id: 00000000-0000-0000-0000-000000000000″,”innerError”:{“date”:”2022-08-02T12:42:21″,”request-id”:”8d4d752e-9ae3-4002-b1c7-62595b898033″,”client-request-id”:”8d4d752e-9ae3-4002-b1c7-62595b898033″}}} — End of inner exception stack trace — at Microsoft.Intune.PowerShellGraphSDK.PowerShellCmdlets.ODataCmdletBase.Run() at System.Management.Automation.CommandProcessor.ProcessRecord() — End of inner exception stack trace — at System.Management.Automation.ExceptionHandlingOps.CheckActionPreference(FunctionContext funcContext, Exception exception) at System.Management.Automation.Interpreter.ActionCallInstruction2.Run(InterpretedFrame frame) at System.Management.Automation.Interpreter.EnterTryCatchFinallyInstruction.Run(InterpretedFrame frame) at System.Management.Automation.Interpreter.EnterTryCatchFinallyInstruction.Run(InterpretedFrame frame) at System.Management.Automation.Interpreter.Interpreter.Run(InterpretedFrame frame) at System.Management.Automation.Interpreter.LightLambda.RunVoid1[T0](T0 arg0) at System.Management.Automation.ScriptBlock.InvokeWithPipeImpl(ScriptBlockClauseToInvoke clauseToInvoke, Boolean createLocalScope, Dictionary2 functionsToDefine, List1 variablesToDefine, ErrorHandlingBehavior errorHandlingBehavior, Object… Read more »
Good morning,
We’ve had this working fine for months, but all of a sudden the “Post-Remediation” output has started returning “REDACTED” for > 75% of devices.
Any idea what would’ve caused this?
Thanks
Hi, I Wonder if anyone can help.
We have Intune setup to rename the built in admin account automatically as part of profile setup. It also sets the Local Admin group users up using a custom xml file in Intune.
I would like to introduce laps for security.
So in reality I only need the script to set the account to enabled, PW never expire, account never expire and to rotate the password then output to Intune. Could anyone help me change the script to achieve this please?
Everything is working we can show password but password not change after 1 hours automatically.
Anyone have ideas on how to run the gui.ps1 on an Android? I’ve looked up some guides for running powershell via the Userland app, but I doubt that will allow for the GUI to work.
Hi,
Great solution this, the one issue I seem to have is the sync’s. So I set the remediation to every hour, however the password remains the same the next day. Does it need a reboot for this to kick in? If so, could this become unsafe if the user could potentially have the local admin password until the device is rebooted?
Thanks,
A
I’ve noticed LAPS has stopped working. Been like this for a few weeks now. It does not actually run on the device. There are no Pre or Post-remediation errors.Seems the script is running somewhat successfully but I can’t use the password.I can see it is not running every hour…even after device syncSome devices that have just been synced show the last run a few days ago. But that is not the main issue I guess, when I try to use the password it does not accept it. Any suggestions? Not sure if Windows has changed something or some other thing… Read more »
can you please explain how to create GUI.
This is a fantastic solution that I’d love to implement in my organization. However, my organization does allow a rather extensive list of users with legitimate needs to have admin rights (at least temporarily), and we’re not ready to implement a more robust solution (yet). As such, maintaining the list of SIDs is exhausting, since the list often changes. In my scenario, the users are maintained in two groups synced to AAD from AD (one for permanent admin rights and one for temporary 5 day rights). In the old days, the groups were GPO added to ALL workstations (because of… Read more »
Hello I get the following error when running the GUI as Intune Administrator or Service Desk users.
************** Exception Text **************
System.Management.Automation.CmdletInvocationException: HttpRequestError —> Microsoft.Intune.PowerShellGraphSDK.PSGraphSDKException: HttpRequestError —> System.Net.Http.HttpRequestException: 401 Unauthorized
{“error”:{“code”:”UnknownError”,”message”:”{\”ErrorCode\”:\“Forbidden\“,\”Message\”:\”{\\r\\n \\\”_version\\\”: 3,\\r\\n \\\”Message\\\”: \\\”An error has occurred – Operation ID (for customer support): 00000000-0000-0000-0000-000000000000 – Activity ID: a4df0c5f-56e7-4362-98f5-83b96629d82a – Url: https://fef.msub05.manage.microsoft.com/DeviceFE/StatelessDeviceFEService/deviceManagement/deviceHealthScripts%28%2710c1b6a4-add4-4334-b8fe-7820c2362ab4%27%29/deviceRunStates?api-version=5022-04-14&$filter=managedDevice%2fdeviceName+eq+%27weazl-gyr4hr2%27&$select=postRemediationDetectionScriptOutput&$expand=managedDevice(%24select%3ddeviceName%2coperatingSystem%2cosVersion%2cemailAddress)\\\”,\\r\\n \\\”CustomApiErrorPhrase\\\”: \\\”\\\”,\\r\\n \\\”RetryAfter\\\”: null,\\r\\n \\\”ErrorSourceService\\\”: \\\”\\\”,\\r\\n \\\”HttpHeaders\\\”: \\\”{\\\\\\\”WWW-Authenticate\\\\\\\”:\\\\\\\”Bearer realm=\\\\\\\\\\\\\\\”urn:intune:service,c3998d6e-2e37-4c56-87b5-7b444ee1cb26,f0f3c450-59bf-4f0d-b1b2-0ef84ddfe3c7\\\\\\\\\\\\\\\”\\\\\\\”}\\\”\\r\\n}\”,\”Target\”:null,\”Details\”:null,\”InnerError\”:null,\”InstanceAnnotations\”:[]}”,”innerError”:{“date”:”2022-06-09T08:11:05″,”request-id”:”a4df0c5f-56e7-4362-98f5-83b96629d82a”,”client-request-id”:”a4df0c5f-56e7-4362-98f5-83b96629d82a”}}}
If I run with a GA account it works fine. Any ideas what permission is required?
I noticed just recently that this is reporting a new password but the devices themselves aren’t having the reported passwords applied to them.
If I delete a device from intune, how do I then use the LAPS tools to log into the device with the local admin account? It seems the LAPS data also deletes when the device is deleted.
it looks like the script query you need to run to get a list of your remediation scripts no longer works (at least not for me) it just returns an error. https://graph.microsoft.com/beta/deviceManagement/deviceHealthScripts
Generally this works very well, occasionally the device will not accept the admin password. What do you recommend we do to troubleshoot when that happens?
[…] Lean LAPS […]
Hey Jos,
This works like a charm.
Can you please explain the purpose of line 177 and what it does?
“$res = Set-Content -Path $markerFile -Value (ConvertFrom-SecureString $newPwdSecStr) -Force -Confirm:$False”?
Why is the script writing to temp?
Thanks again for the awesome script.
Great concept! I tested this initially with no encryption. I also upgraded your solution by converting the .ps1 to an .exe by using a PS1 to EXE generator and included an icon for the app. I did this to prevent the script from being modified or changed by inexperienced support personnel. After my initial test, however, I tried using the encryption process but I am having issues when attempting to encrypt the password. I have configured the private and public keys in their respective areas of the scripts. The password is encrypted into MEM, but when running the gui.ps1 script… Read more »
Great work! Thank you!
But I noticed that built-in administrator doesn’t disable if I set up $disable Builtin Admin Account = $True
Where can be a problem ?
Hi! I’m utilizing this within my company. I’m getting the incorrect username and password error when attempting to use the local admin account. This is some pretty great stuff and any help will be appreciated!
What kind of rights are needed to run the GUI.ps1 script? I get the request to login with my admin account, but seems like my credentials aren’t enough to run it.
Thanks! This is very useful! I’m trying to implement this in our environment, however I noticed the Local admin created by the script has the tendency to recheck its “User needs to change password at next logon” setting every now and then, thus making the password useless. Any advice on that?
This is a great solution, is there a way can we get the logs for audit purposes, who used the passwords and when on which device did they use something like this?
Works the 1st time it runs but after that the script Pre-remediation detection output says it failed because the specified local admin account already exists. Is anyone else having this issue? Do I need different detection and remediation scripts?
Hi I have an error with the GUI , can you help ?
Hello!
Ive been trying to use your script. It seems towork but when i go to Post-Remedition Detection output all I get is the attache screenshot with a string of numbers….all i changed in the script was the admin account name and $minimumPasswordLength = 10 not 21
Am i doing something wrong?
Cheers
Jos, this is amazing and working flawlessly for locally created user accounts, any thoughts on how to remove the AzureAD\Username accounts? getting the following errors about the account not being found.
Hi, Love the script but, I seem to have one issue where it creates the local admin account as disable vs. enabled. Any one have any ideas as to why? or experience similar issues?
I tried adding :
Enable-LocalUser -Name “InsertAdminAccountNamehere”
at line 98 but no luck
Hi Jos,
Good work, I have tested and everything is working as expected.
I work for an MSP and would love to deploy this solution to our clients to replace on-premises LAPS as we complete cloud migrations. This isn’t something we are looking to sell, just a tool to use as a replacement for on-premises LAPS. I understand you need to give consent to allow us to use this tool before we do.
Thanks,
Gary.
I’ve been using this solution for a couple of weeks now. But I started seeing some endpoint gving me this Post-remediation detection output:
REDACTED
What could be causing this ?
This is the output from the gui tool
Local Username : .\REDACTED
Password : REDACTED
Password Changed : REDACTED
I have this set to run Daily and repeat every 30 days and have it assigned to all my devices. However, in the device status page I’m seeing it being run multiple times a day with different username’s associated with the status. This makes it very hard to determine what the current password is if I have to check 3-4 different outputs to determine the password. Any reason why I’d be seeing this?
I am getting this error when trying to run the GUI…any thoughts ?
Hi Jos! Hope all is well! Been testing the new encryption option and running into an issue with the GUI. I loaded your old GUI I had working with the previous laps version without encryption and the old gui shows multiple logons if the machine had multiple users and also the different times the password was updated. The new GUI will only show 1 result and is the first result. Never any of the new password syncs show. I can see the passwords being updated in the intune portal. I made a fresh machine to test as well and same… Read more »
[…] LeanLAPS […]
Does any one have instruction how to install this GUI?
Hi,
this works great. I set the script to run every 1 hour to check logs frequently…However, it happens on some machines that scheduled task just stopped working and never clears the log file. Is there any way to troubleshoot this? I can’t even see it within missed runs using:
Get-ScheduledTask | Get-ScheduledTaskInfo | ? NumberOfMissedRuns -gt 0
Scheduled task is not listed there.
Groeten!
The tool is great, thank you.
I have just one issue after implementing it:
I can’t execute elevated apps with AD admin accounts anymore.
A dialog box opens that the domain admin does not have sufficient rights to start the elevated process, ie. cmd.exe.
Elevating processes is now only possible by using the local admin account.
Is this behaviour a known issue?
Dear,
I have an issue, when I check I see that some laptops with one entry and others with two entries for the same laptop.
Do you have an idea how we can modify the script so it fixes this issue?
Note the two entries will work fine (one of them) but not the only one entry.
Thanks in advance
Hi,
great script, and it works nice, but I’ve one question.
when the script is running, I see the password in plain text in the registry.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\IntuneManagementExtension\SideCarPolicies\Scripts\
after 5 min. the password is removed and changed to REDACTED.
Is it possible to change this faster?