While playing around with PHP (experimental support) in Azure Functions, I noticed that there is no documentation yet and very few examples, so here’s my first simple example on how to build an Azure Function using PHP to parse a very simple GET request.
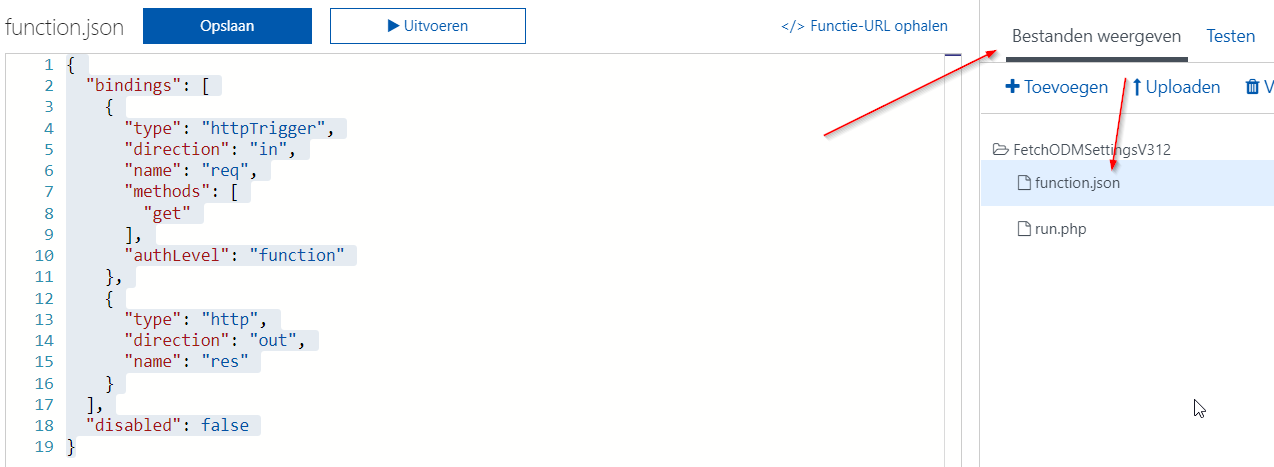
I’m assuming you’ve set up your function, go into Files and edit the function.json file:
{
"bindings": [
{
"type": "httpTrigger",
"direction": "in",
"name": "req",
"methods": [
"get"
],
"authLevel": "function"
},
{
"type": "http",
"direction": "out",
"name": "res"
}
],
"disabled": false
}
This sets the function to listen to get requests and ignore the default Azure Table storage stuff.
Then open the run.php file and Continue reading Parsing a GET request in PHP with an Azure Function