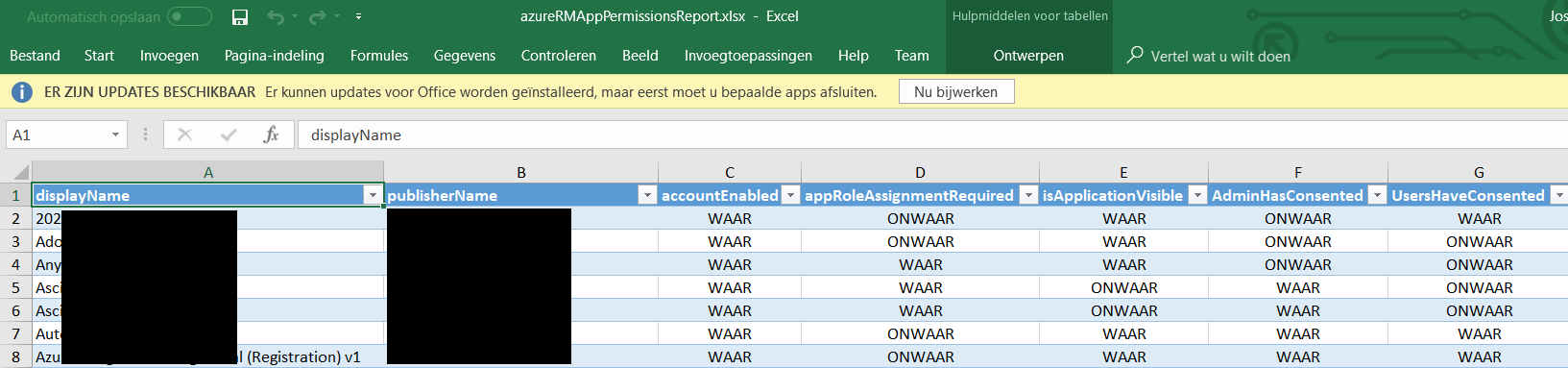
So you’d like to know which applications are living in your AzureAD?
And you’d like to know which of those were added by your admins, and what permissions those applications have?
And you’d also like to know which applications your users are consenting to, and what rights those applications have on your users?
Look no further, I wrote a script to export all of that to Excel for you!
Apps an admin has consented to and the type of rights it needs
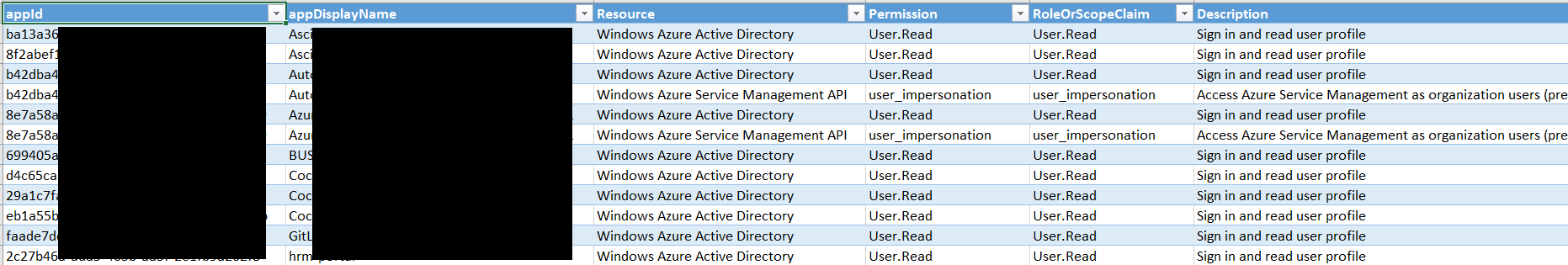
Apps a user has consented to and the type of rights it needs
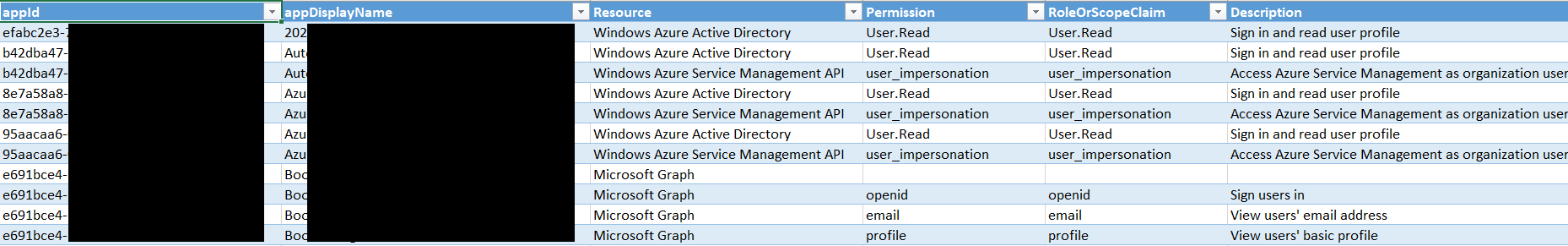
Apps to user mapping, for an easy overview of which user has consented to which app
Get it at:
Credits to Doug Finke for the Excel module I’m using!