Let’s face it, Microsoft’s documentation on using Sharepoint as a data source (or sink) in ADF is pretty bad. And it doesn’t even describe how to use the Managed Identity of ADF, who still wants to register separate app credentials? Noooooo you don’t.
So here’s an example how to use Managed Identity to read a json file from a given SpO site, using minimal permissions given to ADF.
- Enable MI in datafactory, I’m assuming you know how to do this.
- Give ADF Sites.Selected Graph permissions, e.g. like this:
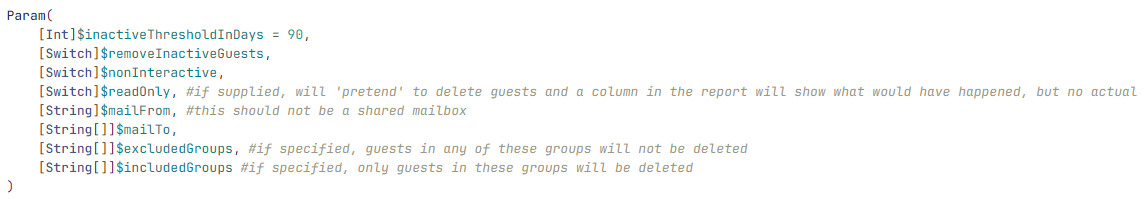
Param(
[Parameter(Mandatory=$true)][String]$displayName="{NAMEOFADFINSTANCE}",
[Parameter(Mandatory=$true)][String]$role="Sites.Selected"
)
Connect-AzureAD
$Msi = (Get-AzureADServicePrincipal -Filter "displayName eq '$displayName'")
Start-Sleep -Seconds 10
$baseSPN = Get-AzureADServicePrincipal -Filter "appId eq '00000003-0000-0000-c000-000000000000'"
$AppRole = $baseSPN.AppRoles | Where-Object {$_.Value -eq $role -and $_.AllowedMemberTypes -contains "Application"}
New-AzureAdServiceAppRoleAssignment -ObjectId $Msi.ObjectId -PrincipalId $Msi.ObjectId -ResourceId $baseSPN.ObjectId -Id $AppRole.Id
$Msi.AppId
- Go to https://yourtenant.sharepoint.com/sites/yoursite/_api/site/id and copy the Edm Guid:

- Go to https://developer.microsoft.com/en-us/graph/graph-explorer. Log in at the top right using a user with sufficient permissions, set the mode to POST, add the EDM guid in the URL and create the request body as follows (the id in the body can be found back in step 2, $Msi.AppId)

- Create a REST linked service in ADF with Managed Identity auth:

- Create data source in ADF of type REST

- Replace the “uri” with the direct url of the file you want to read (or use an alternative method). Example uri:
https://graph.microsoft.com/v1.0/sites/ee614b6d-de15-4101-1c12-14e4cd3186a9/drive/root:/General/Input_files/test.json:/content