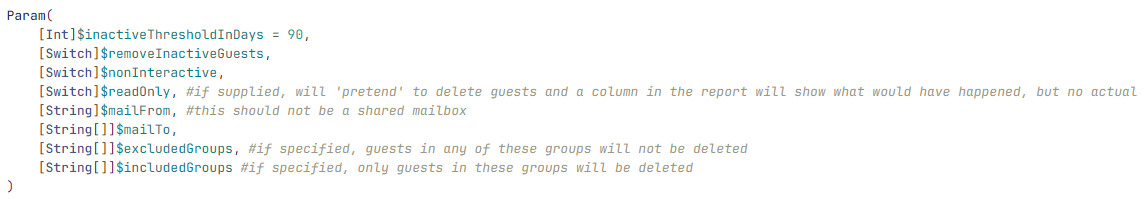
I’ve added basic multi-threading to ADDRS: https://www.powershellgallery.com/packages/ADDRS/1.1.8
This solely ensures that the most compute intensive task (caching sizes/performance) is not repeated between jobs. You’ll still have to handle running multiple jobs using your own preferred method, e.g. foreach -parallel, runspaces or start-job. Example:
$scriptBlock = {
Param(
$vm,
$measurePeriodHours,
$workspace,
$token
)
import-module ADDRS -force
Login-AzAccount -AccessToken $token.Token -AccountId $token.UserId -Tenant $token.TenantId
set-vmRightSize -doNotCheckForRecentResize -targetVMName $vm.Name -domain "lieben.nu" -measurePeriodHours $measurePeriodHours -workspaceId $workspace.CustomerId -Verbose -maintenanceWindowStartHour 22 -maintenanceWindowLengthInHours 3 -maintenanceWindowDay 6
}