When auditing a Sharepoint environment, an important component is permissions;
- invited users
- sharing links
- inherited permissions
- unique permissions
- broken inheritance
- sites, webs
- lists, libraries
I’ve heavily modified Salaudeen Rajack’s work to share a more fully featured and faster PowerShell auditing script that will dump all unique permissions (up to item level, recursively) for all sharepoint sites (including O365 group sites). For files, folders, sites, libraries, etc etc.
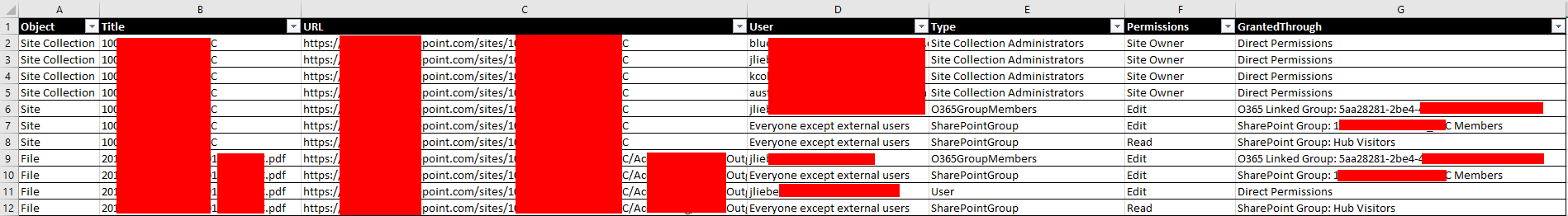
It retrieves membership of groups so the resulting CSV file contains all permissions, with exception of the “Everyone” group, which is listed as a group instead.
You can find the script here: https://gitlab.com/Lieben/assortedFunctions/-/blob/master/get-SPOPermissions.ps1
Usage
- the script uses device based logon, just follow the prompts.
- don’t forget to first set permissions on all sites for your admin account, see script header for an example
- requires the PnP module
- you can exclude specific sites or users from the report if needed, configure siteIgnoreList or principalIgnoreList for that
- Runtime on an environment with over 1000 sites and millions of objects was about 6 hours. If you environment is too large, contact me and I can perhaps introduce e.g. multi-threading.
Can’t tell you how amazing it is to have stumbled across this!
Question: What if the account is set to “Additional Admin” rather than owner? I am assuming it will still work?
Reason being is the client’s environment, they do not want to see an admin in the members of the Team Site – by adding the admin as an additional admin of a SharePoint site we can avoid the admin being a true “member/owner” of the site.
The script is now totally broken:
IMPORTANT – Code Samples | Microsoft Learn
Needs the auth part updated.
Thanks for modding this script, it looks great. I’m no PowerShell expert so it took some time to figure out how to get the SharePoint Online Management Shell in Windows 11, which uses PS 5.1, to work with PnP.PowerShell (had to force install 1.12.0 since everything after that relies on PS 7.2, which doesn’t with with the legacy SharePoint Online Management Shell). Now I’ve done that, for every site I get popups like the attached. As soon as I say “No” to the script error, the Site Settings page disappears and the script continues, but it just keeps happening. Why… Read more »
Hi Jos,
I’m getting the error message: Remove-SPOUser : A user may not remove his or her own account from a site collection. At C:\Temp\sharepoint_permissions2.ps1:494 char:5 + Remove-SPOUser -Site $SitesCollections[$s].Url -LoginName $userUP … + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : NotSpecified: (:) [Remove-SPOUser], ServerException + FullyQualifiedErrorId : Microsoft.SharePoint.Client.ServerException,Microsoft.Online.SharePoint.PowerShell.Remov eSPOUser
Any idea how to resolve this? My user is now admin on all SharePoint’s and OneDrive sites which is not idea.
Hi Jos, many thanks for this script! This has saved us an enormous amount of work. We do run into the fact that it seems that the members of a group are not being read. We have placed an O365 group and a security group in a SharePoint group. Both groups are shown in the output, but not the members of either group. Do you have any idea why?
Hi Jos, currently i’m running your script, but since our Tenant seems to have a lot of teams Sites it’s already at 30hours running and not even close to complete, its showing some errors but it keeps going, so i’m ignoring those, the thing is it’s scanning for 2419 sites, but I only need the ones on our library, and those are like 20 something. On our admin center they are listed on “Classic Sites”. Or if I could run it individually would do the trick as well
Hey Jos – sorry, don’t know how to change the weird purple emogi … delighted with the script, amazed with your patience to write it, and generosity in sharing. One problem: at the end cannot remove the permission added “Remove-SPOUser : A user may not remove his or her own account from a site collection.”
For me the script runs into the following error:
Error Generating Site Permission Report! Cannot process argument transformation on parameter ‘Web’. Cannot convert the “Microsoft.SharePoint.Client.Web” value of type “Microsoft.SharePoint.Client.Web” to type “Microsoft.SharePoint.Client.Web”
Any idea how to solve this?
Paul,
Sorry for the delay in response.
No I am not able to re-write the script to use a certificate authentication.
Best regards,
Nee2ok
Jos,
I have just stumbled on this great script that I would like to test.
However, I am a PowerShell newbie.
How would I modified the authentication with AppId, CertThumbprint, TenantId if I do not want use DeviceCode
Thanks in advance
In my environment the “SharedWithUsers:SW” was very unreliably populated in the MetaInfo. So your script, whilst very speedy, only gave very partial results. I don’t doubt the accuracy of the results I did get however; they just are far from complete.
Looking at this article:
Shared With column displays users who no longer have access to a document – SharePoint | Microsoft Docs
it would seemt that this propery is somewhat hit and miss and perhaps best avoided.