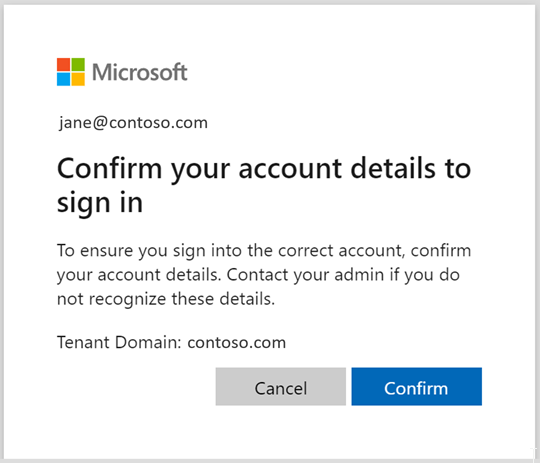
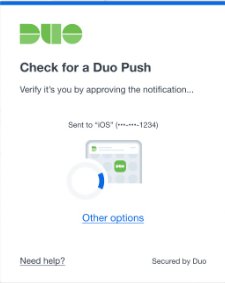
Teams Room accounts are usually excluded from conditional access. To do so, they have to be in a security group, which of course we don’t want to do manually.
Most companies choose to use a naming standard and simply use that as a rule to create an exclusion group. This is easy to circumvent, I can create a guest user / get invited with the right name et voila zero CA policies!
A better way is to identify the accounts based on their assigned licenses, e.g. Teams Rooms Basic (6af4b3d6-14bb-4a2a-960c-6c902aad34f3). This, however, is not supported as an Azure AD group membership rule as this is stored in the AssignedLicenses property which will throw an “Unsupported Property” error.
The assignedPlans property however does contain the GUID we need.
The following Azure AD Group dynamic membership rule only matches users that have a Teams Room Basic, Teams Room Standard or Teams Room Pro license:
(
(
user.assignedPlans -any (
assignedPlan.servicePlanId -eq "8081ca9c-188c-4b49-a8e5-c23b5e9463a8"
-and
assignedPlan.capabilityStatus -eq "Enabled"
)
) -or
(
user.assignedPlans -any (
assignedPlan.servicePlanId -eq "ec17f317-f4bc-451e-b2da-0167e5c260f9"
-and
assignedPlan.capabilityStatus -eq "Enabled"
)
) -or
(
user.assignedPlans -any (
assignedPlan.servicePlanId -eq "92c6b761-01de-457a-9dd9-793a975238f7"
-and
assignedPlan.capabilityStatus -eq "Enabled"
)
)
) -and not (
user.assignedPlans -all (assignedPlan.servicePlanId -eq "")
)
if you want to do something similar for other licenses, here are the options/combinations:
https://github.com/MicrosoftDocs/entra-docs/blob/main/docs/identity/users/licensing-service-plan-reference.md