It is best practise in IT to secure access to resources with Groups.
Membership of a security group means access to whatever resources are secured by that group. Sometimes these groups are self-managed by an owner, sometimes centrally.
In all cases, fairly low privileged users, that are not global admins, can add users to these groups including themselves. Imagine that you have a group called ‘Global Admins’, and your helpdesk user assigns himself to that group. You’d like to know right?
With Privileged Access Groups in Azure AD (Preview) you can protect groups like these actively, but, this requires a P2 license and still lacks some customization features.
An alternative method is to use a simple alerting rule in MCAS (Microsoft Cloud App Security), where you set an alert when ‘someone’ joins a specific group, or if you want to do more than alerting you could also run an automation playbook.
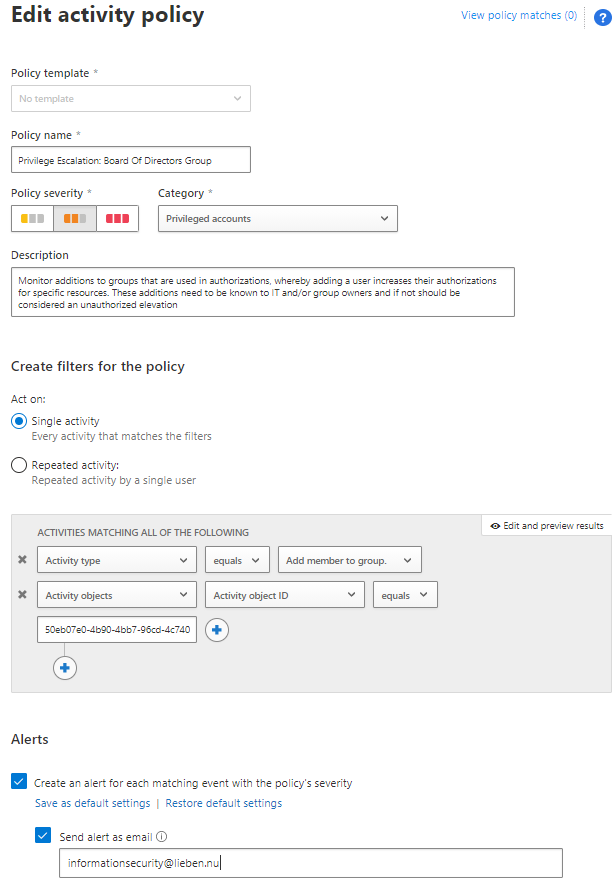
Here’s how to protect a specific Azure AD or Office 365 group with MCAS:
- look up its GUID in AzureAD
- Create an Activity Policy in the MCAS console
- Specify the group GUID as ‘Activity object ID’ in the policy and the correct action type: