- Use local device (azure ad) certificate when needed
- If a mapping fails, don’t stop but try to map other defined mappings
- Bugfix for MFA auth
- Add an intranet site entry to prevent copy/paste warnings
- Improvements to device auth/conditional access handling
Monthly Archives: March 2019
Programmatically triggering a group licenses refresh for AzureAD
Azure AD allows us to assign licenses to groups, a nifty feature that has made a host of automation scripts dealing with bulk license assignment obsolete.
A problem I’ve encountered is that when you assign users to a group, license assignments are not processed right away, especially if you didn’t have enough licenses when you assigned the user to the group (and added licenses to the tenant later).
Azure AD has a button to trigger an update manually:
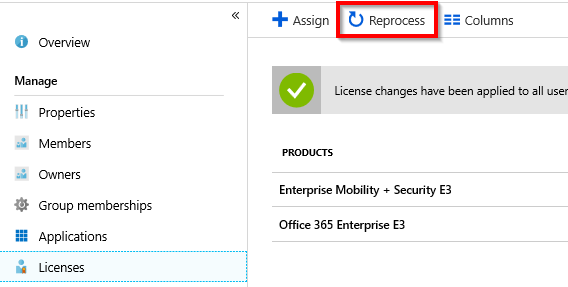
But of course, this can also be automated with PowerShell!
function Invoke-AzHAPIReprocessGroupLicenses{
<#
.SYNOPSIS
reprocesses group license assignment
.NOTES
Author: Jos Lieben
.PARAMETER AzureRMToken
Use Get-azureRMToken to get a token for this parameter
.PARAMETER groupGUID
GUID of the group to reprocess licenses of
Requires:
- Global Administrator Credentials (non-CSP!)
- AzureRM Module
- supply result of get-azureRMToken function
#>
param(
[Parameter(Mandatory = $true)]$AzureRMToken,
[Parameter(Mandatory = $true)]$groupGUID
)
$header = @{
'Authorization' = 'Bearer ' + $AzureRMToken
'X-Requested-With'= 'XMLHttpRequest'
'x-ms-client-request-id'= [guid]::NewGuid()
'x-ms-correlation-id' = [guid]::NewGuid()
}
$url = "https://main.iam.ad.ext.azure.com/api/AccountSkus/Group/$groupGUID/Reprocess"
Invoke-RestMethod –Uri $url –Headers $header –Method POST -Body $Null -UseBasicParsing -ErrorAction Stop -ContentType "application/json"
}
Source on GIT: https://gitlab.com/Lieben/assortedFunctions/blob/master/invoke-AzHAPIReprocessGroupLicenses.ps1https://gitlab.com/Lieben/assortedFunctions/blob/master/invoke-AzHAPIReprocessGroupLicenses.ps1
Disclaimer: the ‘hidden azure api’ is not officially supported.
Requires output from the Get-AzureRMToken function
Get an Office365 / Azure AD tenant ID from a user’s login name or domain
I often need a tenant ID for a given customer, the usual method to get it is to log in to the Azure portal and find it there. But what if you want to get the tenant ID programmatically? Without actually logging in? And you only know the log in name of a user? Or just one of the customer’s domain names?
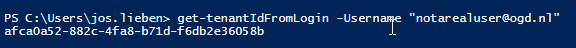
Then this’ll help you out!
function get-tenantIdFromLogin(){
<#
.SYNOPSIS
Retrieves an Office 365 / Azure AD tenant ID for a given user login name (email address)
.EXAMPLE
$tenantId = get-tenantIdFromLogin -Username you@domain.com
.PARAMETER Username
the UPN of a user
.NOTES
filename: get-tenantIdFromLogin.ps1
author: Jos Lieben
blog: www.lieben.nu
created: 8/3/2019
#>
Param(
[Parameter(Mandatory=$true)]$Username
)
$openIdInfo = Invoke-RestMethod "https://login.windows.net/$($Username.Split("@")[1])/.well-known/openid-configuration" -Method GET
return $openIdInfo.userinfo_endpoint.Split("/")[3]
}
Obviously, you can also get the tenant ID by just filling out bogus info in front of the user’s login (e.g. bogus@ogd.nl), it’ll still work as only the domain part of the login is really used.
Hope this helps someone 🙂
Git link: https://gitlab.com/Lieben/assortedFunctions/blob/master/get-tenantIdFromLogin.ps1