It has long annoyed me that all the scaling options in Azure just add and remove hosts. They never target the host itself. Hosts are either under or overutilized in 84% of the case.
And this is especially relevant for AVD personal hostpools where users each have their own personal “VDI”.
So I’m releasing a custom PowerShell module called “ADDRS” (Azure Data Driven Right Sizing) that grabs mem/cpu performance of the VM or all VM’s in a resource group you tell it to check. It will then do some smart voodoo magic to determine what size out of an allowlist best fits.
Instructions / Example:
- Use -WhatIf if you don’t want it to resize the VM
- Use -Force if you want to resize a VM even if it is online (which will cause it to be shut down!)
- Use -Boot if you want the VM to be started after resizing (by default it will stay deallocated)
- Use -domain with your domain if your VM is domain joined
- Use -region if your region is not westeurope
- Use -Verbose if you want the full output incl financial projection
- Use -Report if you want to output data to csv. Can be used together with -WhatIf
- Modify minMemoryGB, maxMemoryGB, minvCPUs, maxvCPUs as desired for your usecase
- You can adjust the preconfigured allowedVMTypes array to only allow specific VM types, by default it contains “Standard_D2ds_v4″,”Standard_D4ds_v4″,”Standard_D8ds_v4″,”Standard_D2ds_v5″,”Standard_D4ds_v5″,”Standard_D8ds_v5″,”Standard_E2ds_v4″,”Standard_E4ds_v4″,”Standard_E8ds_v4″,”Standard_E2ds_v5″,”Standard_E4ds_v5″,”Standard_E8ds_v5”. Overwrite it by using the following parameter:
-allowedVMTypes @(“Standard_D4ds_v4″,”Standard_D8ds_v4”) - use -maintenanceWindowStartHour, -maintenanceWindowLengthInHours and –maintenanceWindowDay if you want to ignore performance data during a maintenance window (e.g. for patching) as that isn’t representative
- Set an Azure Tag called LCRightSizeConfig with the value disabled on machines you want to ignore
- Set an Azure Tag called LCRightSizeConfig with a machine type value (e.g. “Standard_D4ds_v4“) if you want to lock a specific size for that machine, this can be useful if you want the script to resize from current to target automatically when it runs while the VM has been deallocated.
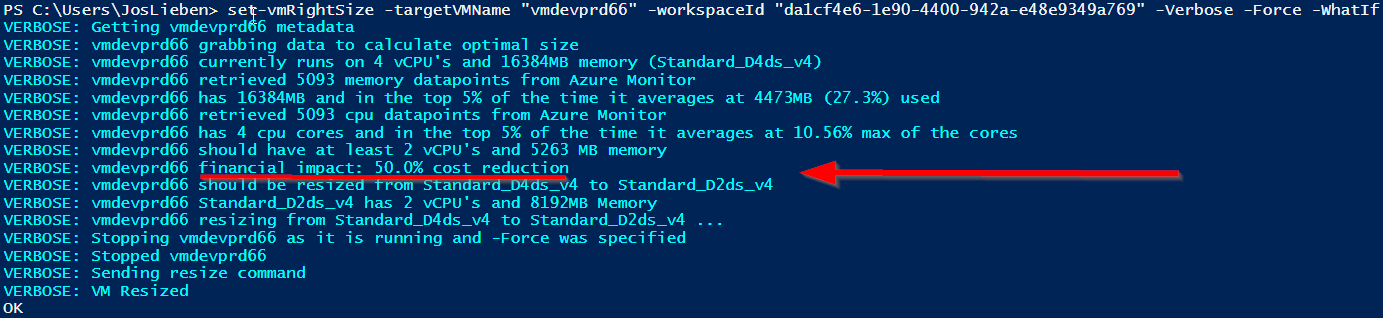
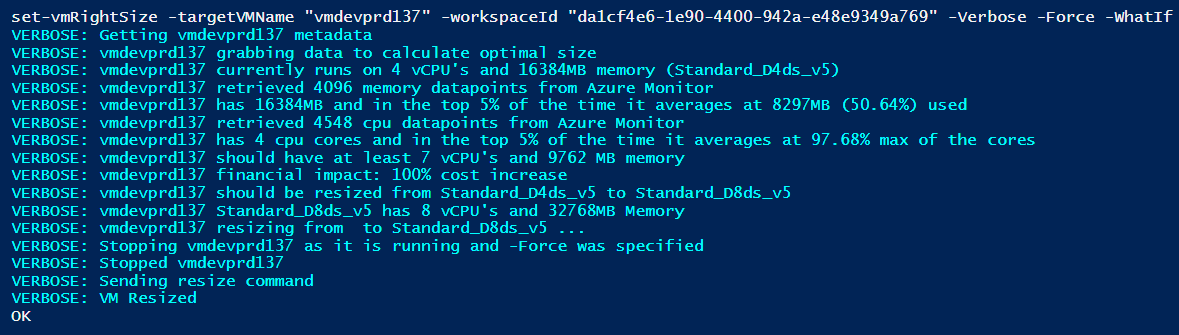
Example -Verbose output of two VM’s being resized:
Requirements:
The module requires that you’ve added the % Processor Time and Available MBytes performance counters to Log Analytics:
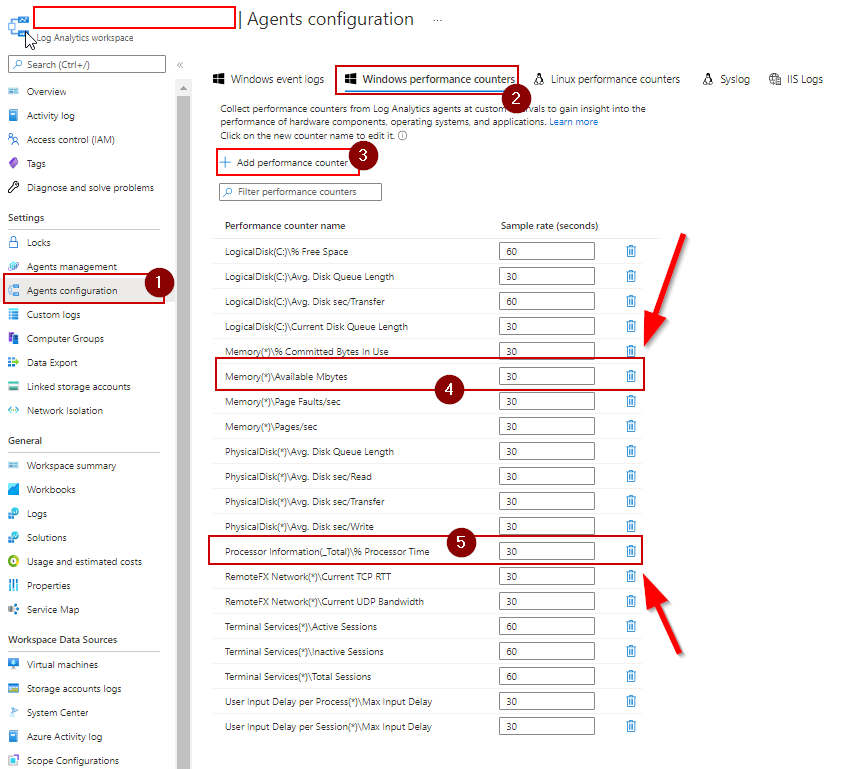
and that your host(s) have the Azure Monitor agent installed.
The module will check if there is sufficient data about the machine in Azure Monitor, if not, no action will be taken. You can determine how far back the function looks by modifying $measurePeriodHours
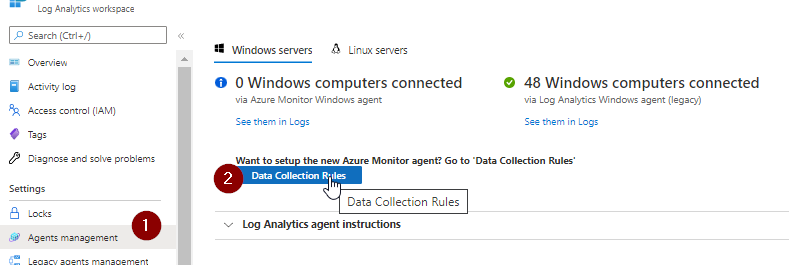
If you’re using the more recent Azure Monitoring agent, add the perf counters here:
Required access
Virtual Machine Contributor to the resource group(s) containing your VM’s and Log Analytics Reader on your log analytics workspace.
Download / Installation
Option 1: Install-Module ADDRS
Option 2: get relevant functions/code from Git
and run the set-vmRightSize or set-rsgRightSize function, e.g.:
set-vmRightSize -targetVMName azvm01 -workspaceId 7ccd0949-2fd4-414e-b58c-c013cc6e445d
set-vmRightSize -targetVMName azvm01 -workspaceId 7ccd0949-2fd4-414e-b58c-c013cc6e445d -allowedVMTypes (“Standard_E8ds_v4″,”Standard_E2ds_v5″,”Standard_E4ds_v5″,”Standard_E8ds_v5”)
set-rsgRightSize -targetRSG rg-avd-we-01 -workspaceId 7ccd0949-2fd4-414e-b58c-c013cc6e445d
Scheduling
If you wish to run this automatically on a schedule, I recommend either using an Azure DevOps pipeline or Automation account. I’ve compiled a small guide on how to use ADDRS in an Azure Automation Account.
Right Sizing Frequency
It is recommended to match job schedules to the lookback period, or at least not run multiple times in the same lookback period. Otherwise, the data that is being used for sizing may not be representative if the machine had already been resized in an earlier run. By default the script will prevent this from happening by checking each vm’s audit log entries.
Issues / notes
- Make sure you’ve got enough data in Log Analytics
- Make sure the allowedVMTypes list contains only VM types that you can actually upgrade to. If e.g. your VM has an ephemeral disk, and your allowList has types that do not, the resize will fail with an error message (but no harm will be done to the existing VM)
- I’ve only tested the maintenance window parameters using UTC time, if you’re using different timezones your results in excluding data generated during the maintenance window may vary from mine
- Spot and Low Priority Azure pricing is excluded by default