With Intune’s new Bitlocker Encryption Report administrators have an effective way of seeing which of their devices have been encrypted.
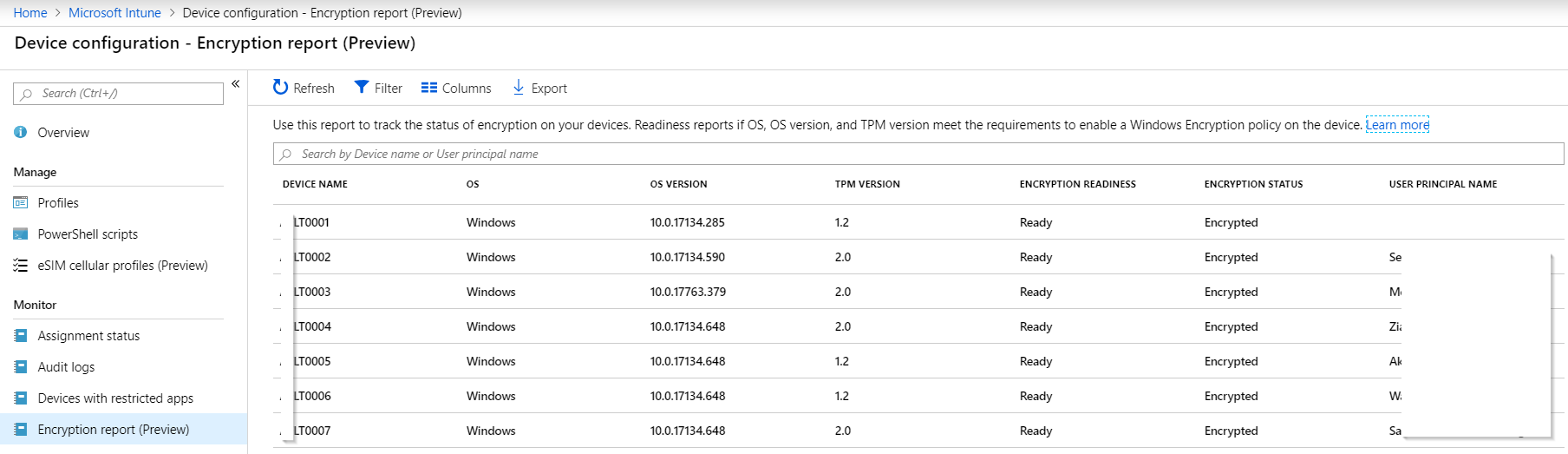
But if we want to know if we can actually recover the bitlocker key of a device, we need to know if it was ever uploaded to AzureAD.
Network or local device issues can sometimes prevent the recovery key from reaching AzureAD, resulting in lost data if the device’s disk needs to be recovered for any reason. To hunt down devices that have not escrowed their recovery key to AzureAD, you can use my report function (in PowerShell as always):
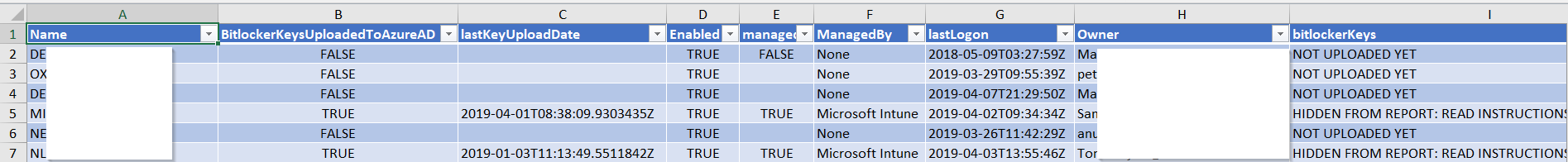
Using Switch -showBitlockerKeysInReport does not show the key in the report. Any advise please?
This has to be run as Global Admin and I added these 3 codes to this function and seems to be working for me
Install-Module -Name importexcel -Force -Verbose -ErrorAction SilentlyContinue
Install-Module -Name AzureRM.profile -RequiredVersion 5.8.2 -Verbose -Force -AllowClobber -ErrorAction SilentlyContinue
Install-Module azuread -Verbose -Force -ErrorAction SilentlyContinue
Hi
When i run the script, the Microsoft page opens for me to authenticate,
after entering my username,password and code Microsoft then says my account is blocked.
I am admin and running the script as admin
Any suggestions on how to get this to work for me please?
thanx
Hello, it is throwing me the following error, if someone knows the solution I will appreciate it:
Invoke-RestMethod : {“ClassName”:”Microsoft.Portal.Framework.Exceptions.ClientException”,”Message”:”Graph call failed with httpCode=Forbidden,
errorCode=Authorization_RequestDenied, errorMessage=Insufficient privileges to complete the operation., reason=Forbidden, correlationId =
780ee56c-6eb3-4649-aa05-d488e8c89f57, response = {\”odata.error\”:{\”code\”:\”Authorization_RequestDenied\”,\”message\”:{\”lang\”:\”en\”,\”value\”:\”Insufficient
privileges to complete the operation.\”},\”requestId\”:\”4cb80364-9d49-447e-8584-50fe43c5fe40\”,\”date\”:\”2022-10-31T21:21:16\”}}”,”Data”:{},”HResult”:-2146233088,”X
MsServerRequestId”:null,”Source”:null,”HttpStatusCode”:403,”ClientData”:{“errorCode”:”Authorization_RequestDenied”,”localizedErrorDetails”:{“errorDetail”:”Insufficien
t privileges to complete the operation.”},”operationResults”:null,”timeStampUtc”:”2022-10-31T21:21:16.2458403Z”,”clientRequestId”:”780ee56c-6eb3-4649-aa05-d488e8c89f5
7″,”internalTransactionId”:”a98a36e4-788e-46c6-86b6-06fe5660400d”,”tenantId”:null,”userObjectId”:”be2a3bbb-60bb-4039-927a-1ec062d705c8″,”exceptionType”:”AADGraphExcep
tion”}}
[…] Devices that lack a bitlocker recovery key in AzureAD | Liebensraum […]
It´s not working for me. I tried to convert AzureRM to AZ cmdlets with MS migration tool. But no luck. This script must be run as a GlobalAdmin? ( I´m only an IntuneAdmin )
Line |
56 | … shToken = @($context.TokenCache.ReadItems() | where {$_.tenantId -eq …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| You cannot call a method on a null-valued expression.
Line |
58 | … $apiToken = Invoke-RestMethod “https://login.windows.net/$tenantId/oa …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| {“error”:”invalid_request”,”error_description”:”AADSTS900144: The request body must contain the following parameter: ‘refresh_token’.\r\nTrace ID: ff042c93-a0a2-42b1-bb72-69a692f41500\r\nCorrelation ID:
| df000497-edd4-4348-b10d-ad7f7021ce39\r\nTimestamp: 2020-11-18 12:01:00Z”,”error_codes”:[900144],”timestamp”:”2020-11-18
| 12:01:00Z”,”trace_id”:”ff042c93-a0a2-42b1-bb72-69a692f41500″,”correlation_id”:”df000497-edd4-4348-b10d-ad7f7021ce39″,”error_uri”:”https://login.windows.net/error?code=900144″}