At OGD we sometimes have to deal with users that got infected with CryptoLockers and have both automated and controlled systems in place to prevent damage or restore data to any fileshares. An infection on Sharepoint Online or Onedrive has not yet happened, but eventually it of course will and I like to fix things before they break.
As Sharepoint Online and Onedrive for Business natively use versioning on files, you basically have no real risk of losing data to Cryptolockers, your RPO (Restore Point Objective) is 0. However, restoring the previous versions of files is quite a lot of work if done manually, so your RTO (Restore Time Objective) could be weeks or more.
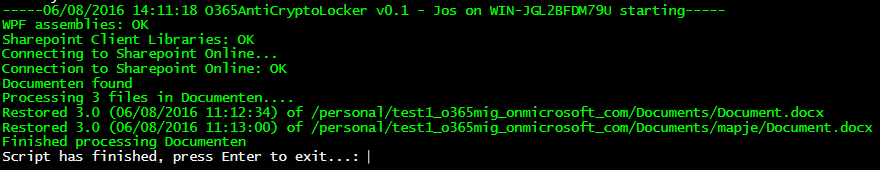
Unless of course, you use Powershell. I’ve written a script that will restore the most current previous version of any file in a given Document Library.
Download: O365AntiCryptoLocker
Example usage for a Onedrive site:
.\O365AntiCryptoLocker.ps1 -siteURL "https://o365mig-my.sharepoint.com/personal/test1_o365mig_onmicrosoft_com" -login "mylogin" -password "mypassword" -libraryTitle "Documents"
Or for a Sharepoint Online Site:
.\O365AntiCryptoLocker.ps1 -siteURL "https://o365mig.sharepoint.com/site1" -login "mylogin" -password "mypassword" -libraryTitle "Documents"
You’ll need the Sharepoint Client Components installed, and you’ll have to have sufficient permissions on the library and its files.