A while ago, you may have read that Microsoft will no longer allow relaying everything by default in Exchange Online when using normal authentication starting in february july 2017.
So I went about and set my SMTP relay in IIS to use a certificate instead, as the article explains. This resulted in a flood of bad mail drops with the following error:
Action: failed
Status: 5.7.57
Diagnostic-Code: smtp;530 5.7.57 SMTP; Client was not authenticated to send anonymous mail during MAIL FROM
After messing around with this for a while, I discovered the outbound port you have to use when connecting to smtp.office365.com to relay a message using anonymous TLS is port 25, NOT port 587 as we were using before to submit mail using a user account + password.
For those who want to configure a relay server on IIS to allow applications and devices that don’t support TLS, I’ll set out the steps to configure this properly:
Preparation
- Order a certificate for one of the domains in Office 365 you own, either a wildcard cert or a cert that has the hostname of your intended relay server in it’s subject name
- a Windows 2008R2 or higher machine
- test accounts
Configuration
-
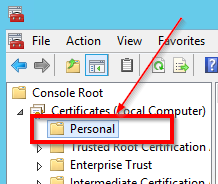
- Import your certificate in the local computer certificate store

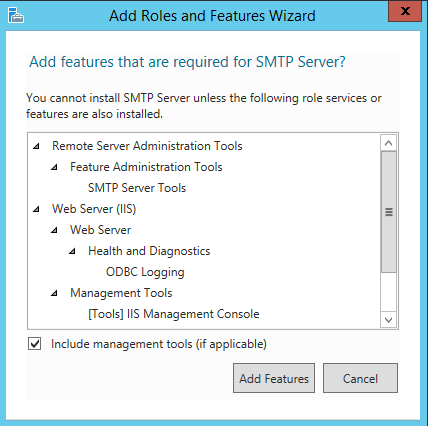
- Install SMTP Server (under Features in the Server Manager). IIS 6 Management Compatibility should be added automatically:
- Configure ‘Connection’ and ‘Relay’ to your preferences, I highly recommend using a whitelist instead of a blanket allow all to prevent infected devices from using this machine to send out spam or worse.
- On the Delivery tab, configure as follows:

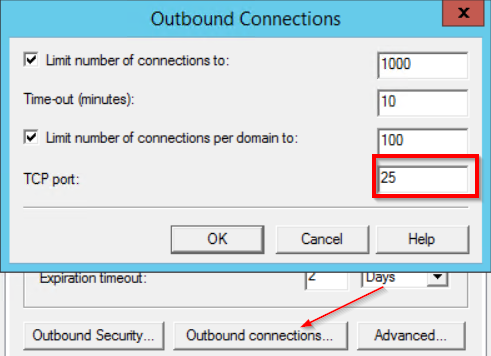
- Configure Outbound connections as well, ensure you set it to port 25:

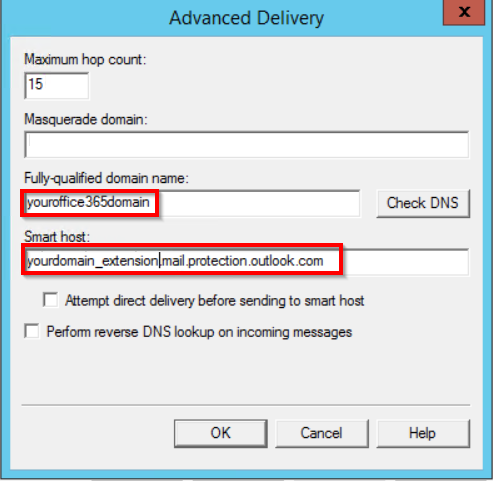
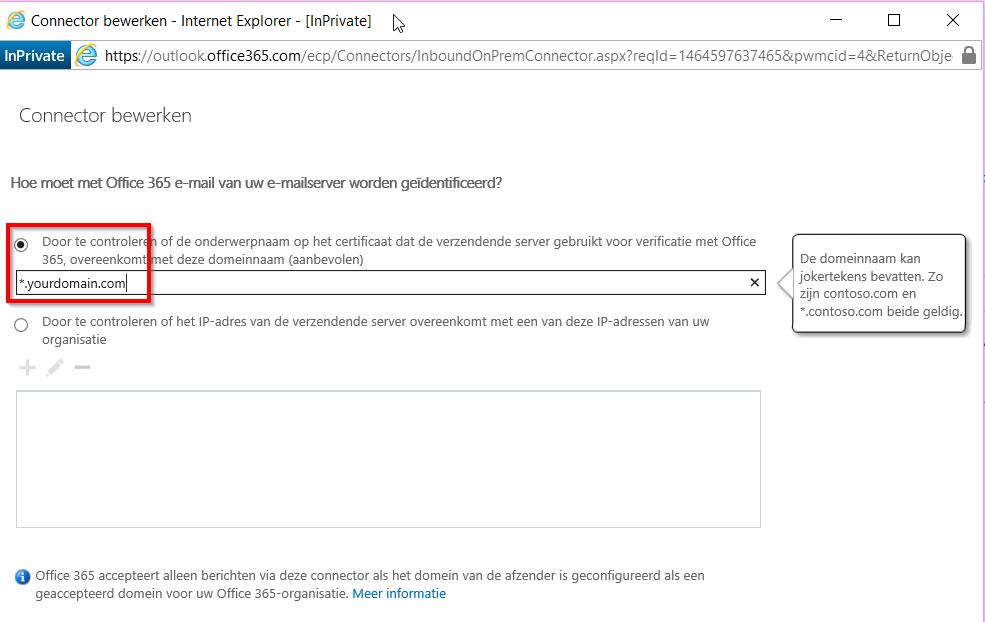
- And configure your hostname and smarthost under Advanced. Make sure the hostname matches the certificate from step 1. The smarthost should match the hostname in the MX record for the domain in your certificate. You can find this under domain properties in Office 365.

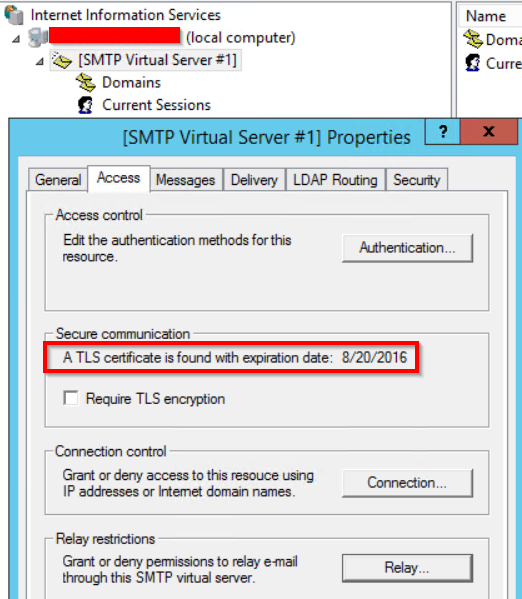
- Restart the SMTP service and open the IIS manager to ensure your certificate was loaded and the expiration date matches:

- Don’t forget to set the connector in Office 365 to certificate based and to test your setup:

- Your server is now ready for use, legacy devices and apps can now submit their mail on port 25, unencrypted, and IIS SMTP will forward it to Office 365 using TLS.
- Import your certificate in the local computer certificate store
This is basically the only supported method to relay email through office 365 without user based authentication.
Further steps
- Depending on your business needs, you may wish to build a second server for load balancing
- Set up monitoring of the badmail folder
- Monitor the eventlog and SMTP service
- Make sure you set a note for yourself somewhere before the certificate expires
- Restrict access to this machine so only trusted apps/devices can send mail

Vielen Dank fuer diese ausfuehrliche Dokumentation von einem deutschen Administrator – So, many thanks for this detailed documentaion from a german admistrator. I was short before giving up …
Great write-up as always.
Ah thank you! This guide saved my bacon today.
[…] you read but did not yet act upon my previous post about changing your relay connectors to certificate based IIS relays , you have another 5 months […]