Microsoft Defender Advanced Threat Protection seems to be becoming the defacto leader in the A/V industry, at least when Windows is concerned, but other OS’es seem to be following quickly 🙂
At one of my international customers, many different locations and departments exist and we’d like to group devices in MDATP based on their primary user so we can assigned different administrators automatically, and apply different web filtering policies.
MDATP has the following options available for grouping:
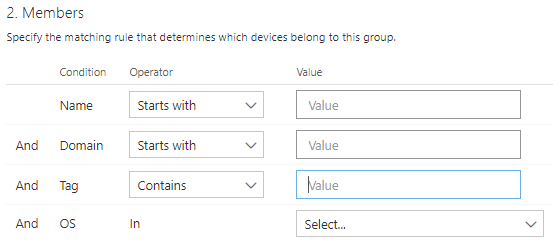
These membership rules don’t say anything about the user, and the machine domains are all cloud native (no hybrid joins). So we need to use Tags to gain flexible targeting in MDATP.
The following PowerShell script can be scheduled as an Azure Runbook to automatically tag all your MDATP devices based on the ‘Company’ attribute of the device’s primary user. It could also be modified easily to e.g. parse a user’s group membership or UPN’s domain.
https://gitlab.com/Lieben/assortedFunctions/-/blob/master/set-MDATPCustomTags.ps1
If you have a lot of devices, it may take a while for the first run (beyond Azure Automation limits), in that case run it locally first and then schedule it.
Hello Joss, trying to use your script and the retrieving of MDE device works fine – but I get a 403 forbidden when trying to update the tag. Any idea why ? the service account I’m using credential off can do the tag change manually, and the app registration has the machine.ReadWrite delegated permission, with admin consent granted for organization.
hey Joss am getting this error trying to see how your script works . Where do i place the credentials as its looking for a way to log into mdatp but i am already authenticates into the portal hoping you can answer Failed to elevated permissions, cannot continue Get-AutomationPSCredential : The term ‘Get-AutomationPSCredential’ is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again. At C:\PS\Defender API\set-MDATPCustomTags.ps1:102 char:18 + $o365Creds = Get-AutomationPSCredential -Name $automationCredenti … + ~~~~~~~~~~~~~~~~~~~~~~~~~~… Read more »