Often we, as cloud admins, need our audit or sign in logs. Usually, we need real-time data because, for example, we’re debugging why that one user has conditional access issues. But sometimes, we need to go back further than 30 days. And that is not something Azure does by default, but can be enabled:
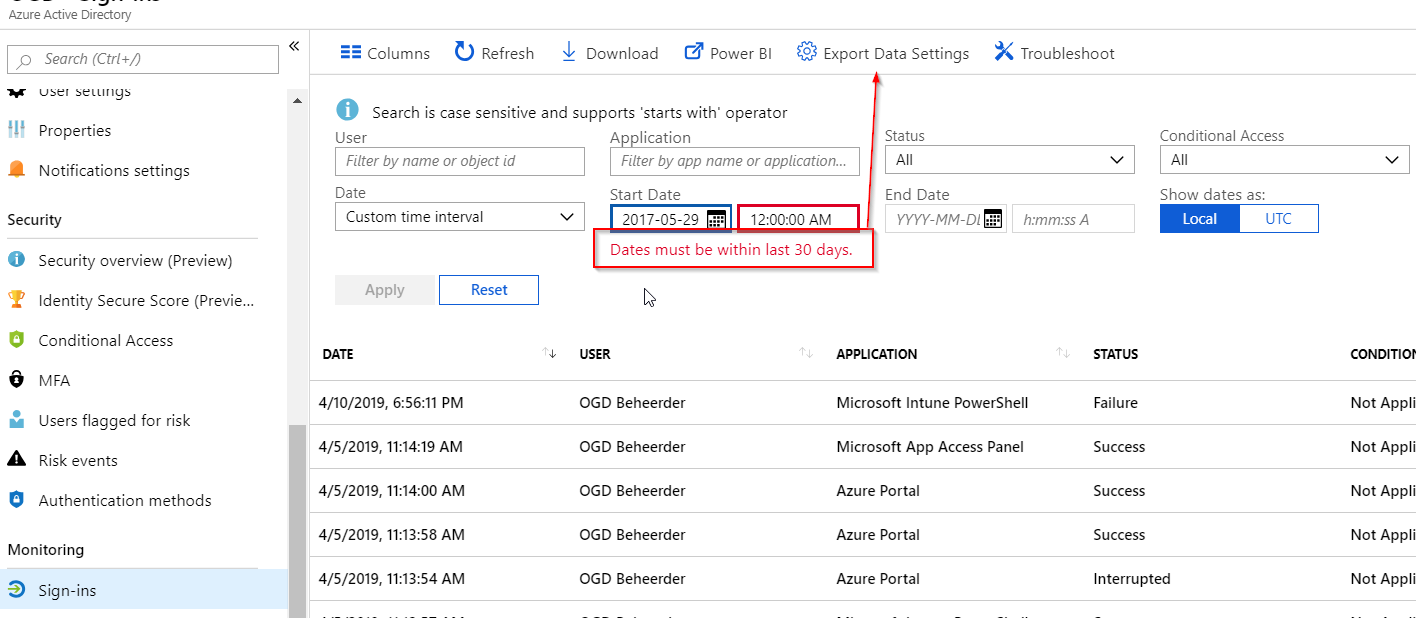
Our options when exporting logs are limited to a Storage account, Log Analytics or an Event Hub. All these options offer multiple extraction methods to cover your transport needs to other systems. The default retention period is then forever, which is nice as we might need audit info going back a bit as hacks are usually discovered after about 206 days.
If you don’t have specific tools or requirements, I recommend setting up a Log Analytics workspace and connecting that to Azure AD:
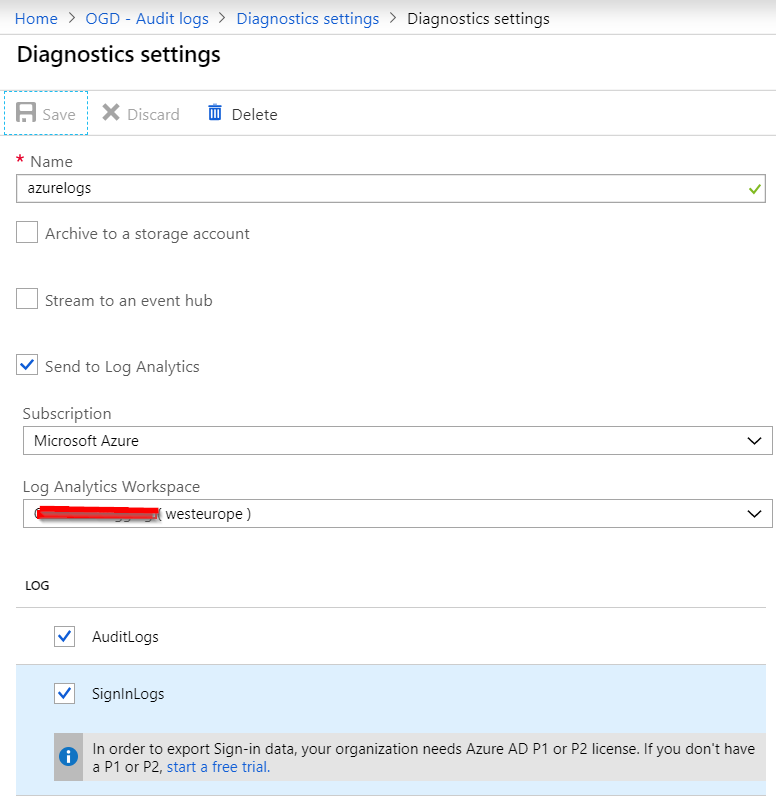
Whichever method you choose, a P1 or P2 license is required. You only need a single license for the entire tenant when using the export audit / singin log functionality of AzureAD. Once configured, the Logs option directly bring you to the Log Analytics workspace search results:
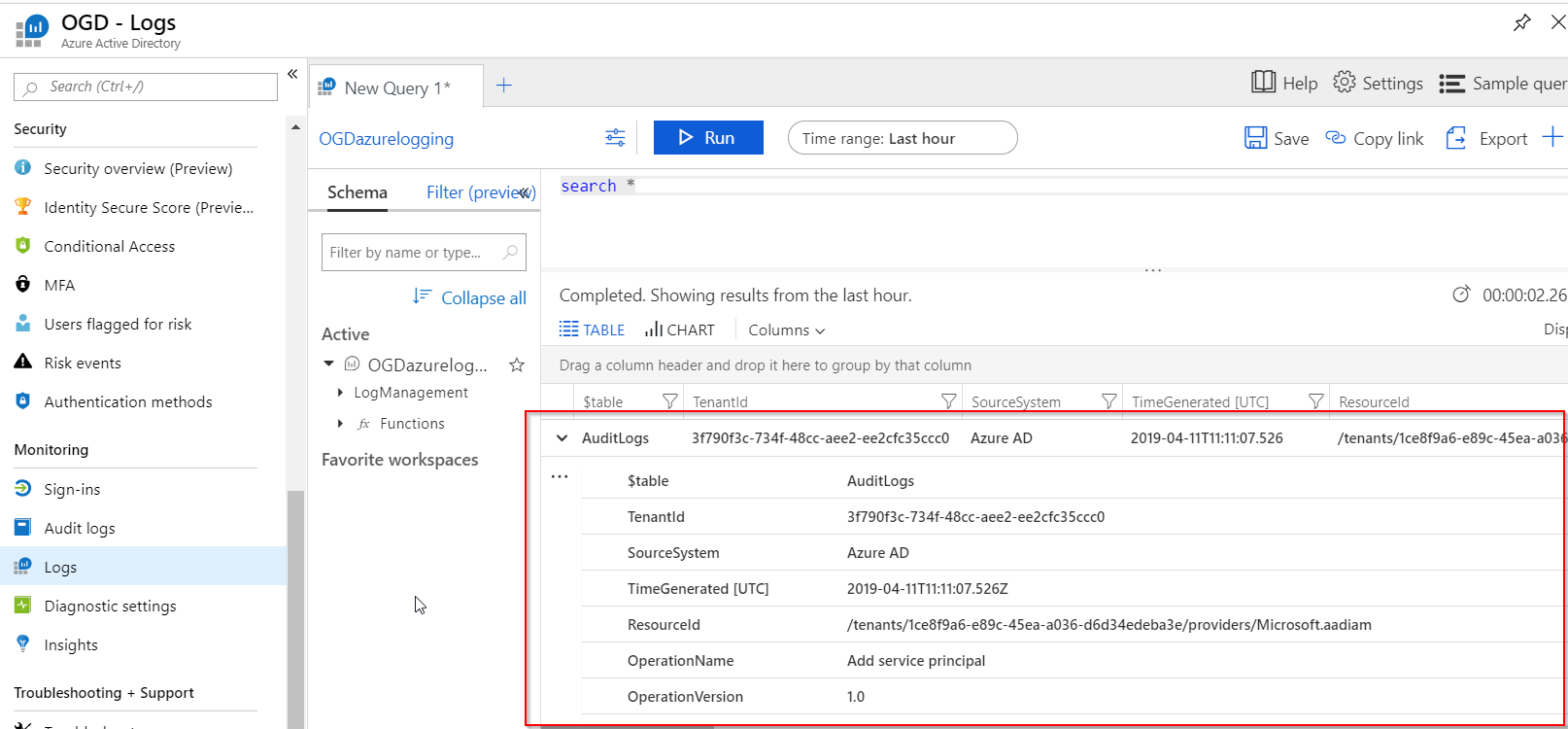
I’ve briefly shown how to configure AzureAD to send audit and sign in logs to Log Analytics so you can go back further than 30 days. Stay tuned for the next post that will utilize these logs to dive deeper into Guest User activity.
just an FYI, you have your OS matching “-NE “Windows”, so that doesnt catch “Windows 10 Enterprise” i switched to -notlike “Windows*”
it also doesnt seem to be catching the same attribute that Microsoft’s own bitlocker report in Intune is capturing. your report shows machines that have bitlocker enabled and recovery keys in Azure as not even being bitlockered.
Maybe microsoft has 2 different places to store this info?
Mike