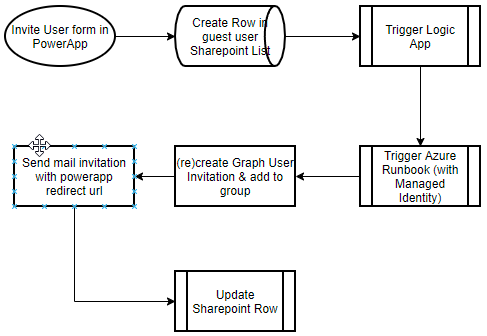
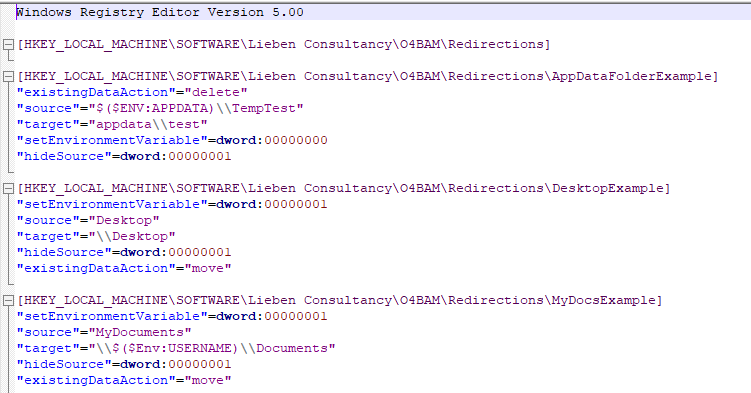
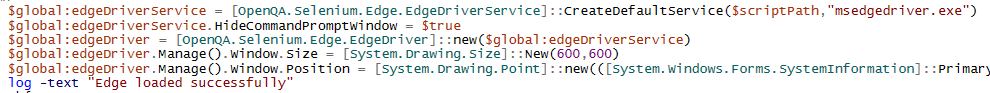
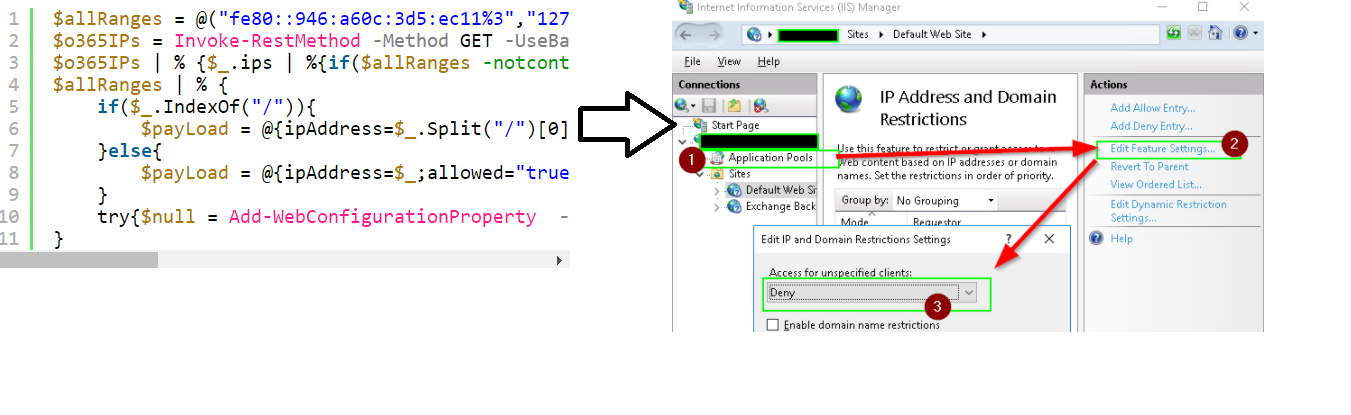
We had an odd case today that Msft support hasn’t fixed yet, but in case someone googles the error and finds this, I did find a workaround.
We had a MailUser object that was inactive (soft deleted), but couldn’t be permanently deleted using
Remove-MailUser -PermanentlyDelete -Identity $mailuser.ExternalDirectoryObjectId
The resulting error was:
This mail enabled user cannot be permanently deleted since there is a user associated with this mail enabled user in Azure Active Directory. You will first need to delete the user in Azure Active
However, nothing was found in AzureAD (or deleted users/recycle bin), and nothing was present in our on-prem AD.
Directory. Please refer to documentation for more details.
This user was deleted a long time ago, and now being rehired….but account creation was being blocked because the mail user was still claiming the email address of this user.
After some messing around, and not patiently waiting for Msft 1st line support to delete this corrupted MailUser, I discovered the RecalculateInactiveMailUser switch in the set-MailUser command.
Normally, you can’t modify the primary smtp / aliases of a soft deleted mailuser or mailbox….BUT, for some reason, if you supply RecalculateInactiveMailUser you can. So:
Set-MailUser -Identity $mailuser.ExternalDirectoryObjectId -EmailAddresses $newProxies -RecalculateInactiveMailUser
Worked fine! While
Set-MailUser -Identity $mailuser.ExternalDirectoryObjectId -EmailAddresses $newProxies
Failed with
The operation couldn’t be performed because object ‘270fc89f-0424-42d2-8f54-25796f74457b’ couldn’t be found on ‘DB8PR02A05DC001.EURPR02A005.PROD.OUTLOOK.COM’.